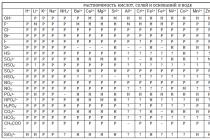
NTFS permissions(NTFS permissions) is a set of special extended attributes of a file or directory (folder) set to restrict user access to these objects. They are available only on volumes where the NTFS file system is installed. Permissions provide flexible protection because they can be applied to both directories and individual files; they apply both to local users (working on computers where protected folders and files are located) and to users connecting to resources over the network.
Not to be confused permissions with rights. These are completely different concepts; for more details, see the Windows NT / 2000 / XP Security Model subsection. Unfortunately, in the technical literature and in everyday life these terms are often confused. This is primarily due to translation errors in the original English-language materials.
NTFS permissions are primarily used to protect resources from local users at the computer where the resource is located. However, they can also be used for remote users connecting to the shared folder over the network. Obviously, in this case, users are affected by two mechanisms for limiting access to resources: first, network, and only then local, file. Therefore, the final access permissions will be determined as the minimum of the network and file permissions... It should be said here that the final network permissions for access to resources that a user will have when working on the network is calculated as the maximum permissions in the list of access permissions, since a user can be a member of several groups that are mentioned in the list. Likewise for NTFS permissions: the user gets the maximum permissions listed in the ACL, and only the No Access permission can cross out all other permissions.
NTFS permissions provide high security selectivity: you can set different permissions for each file in a folder. For example, one user can be allowed to read and modify the contents of a file, another can only read, and a third can be denied access altogether. Note, however, that it is highly recommended that you set permissions on ACLs using group accounts rather than individual user accounts.
Each file object has a so-called access mask(access mask). Access mask includes standard(standard), specific(specific) and generic(generic) access rights.
□ Standard access rights define operations and that are common to all protected objects.
□ Specific access rights indicate the basic rights specific to file objects. So, for example, the specific rights Read_Data, Write_Data and Append_Data allow you to read data, write information and, accordingly, add data to a file. Read_Attributes, Write_Attributes rights
and Read_EA, Write_EA allow, respectively, to read or write attributes or extended attributes of a file or directory. Finally, a specific access right such as Execute allows a file to be executed.
□ Generic access rights are used by the system; they define combinations of standard and specific rights. For example, the generic_Read access right applied to a file includes the following specific and standard rights: Read_Control, File_Read_Data, File_Read_Attributes, File_Read_EA, Synchronize.
So, NTFS permissions are represented differently in the Windows NT 4.0 operating systems and the Windows 2000 / XP family of systems. These differences, first of all, relate to the interface, that is, the Explorer program displays in different ways the permissions that are actually assigned to the file object in the form of access permissions and are processed at the program level. Permissions in Windows 2000 / XP are closer to those specific, standard and generic access rights that we talked about above, but they are not as convenient for controlling access to files as Windows NT 4.0 permissions.
A granular and complex permission system is used to control user access to folders and files. The mechanism for controlling access to Windows objects is one of the most detailed among the known operating systems. For files and folders, there are at least 14 NTFS permissions that can be enabled or disabled - and checked. These permissions can be assigned to files or folders and to users or groups. In addition, you can designate the inheritance order for file or folder permissions and users or groups. It's easy to get lost in the maze of permissions. This article will discuss how folder and file permissions work and the most effective ways to use them.Object Access Basics
The user never comes into direct "contact" with any Windows object. All access to objects is done through programs (for example, Windows Explorer, Microsoft Office) or processes. A program that accesses resources on behalf of a user performs a procedure called impersonation. A program that accesses a remote resource performs a procedure called delegation.
After a user is registered, the System Identifier (SID) and group SIDs are processed by the lsass.exe process, which generates the user's secure access token. Other information is also entered into the secure access token, including the rights (permissions) assigned to the user, the user's session ID (unique for each session), the permission mask with detailed description the type of access requested. The rights assigned to the user can be seen using the command
When a program accesses a protected resource on behalf of the user, the Windows security reference monitor asks the program for the user's secure access token. The Security Monitor then analyzes the token to determine the effective user permissions and allows or denies the user-requested operation. The effective resolutions are described in more detail below.
Share Permissions
Every protected Windows object — including files, folders, shares, printers, and registry keys — supports security permissions. Any Windows folder can be made public to allow remote access. Share permissions can be assigned to any folder and printer object in Windows, but permissions are applied only when the object is accessed over a network share. Folder Share permissions include Full Control, Change, and Read.
Security principals who have been assigned Full Control rights to an object can perform almost any operation on an object. They can delete, rename, copy, move and modify an object. A user with Full Control can change the Share permissions of an object and take ownership of the object (if he is not already the owner and does not have Take Ownership permission). This way, anyone with Full Control permission can revoke the permissions of others, including the administrator (although the administrator can always take back ownership and permissions). The ability to change permissions is a requirement of any discretionary access control (DAC) operating system, such as Windows.
In most cases, the main permission to access a resource required by regular users is Change. With the Change permission, the user can add, delete, modify, and rename any resources in the corresponding folder. Read permission allows you to view, copy, rename, and print an object. A user with Read permission can copy an object to another location in which he has Full Control permission.
NTFS permissions
If Windows uses the NTFS (not FAT) file system, then all files, folders, registry keys, and many other objects have NTFS permissions. NTFS permissions apply to both local and remote access to an object. To view and change the permissions of an NTFS file or folder, just right-click on the object, select Properties, and go to the Security tab.
Table 1 shows the 7 total NTFS permissions. The summary permissions are various combinations of the 14 more granular permissions shown in Table 2. You can view the granular permissions by opening the Advanced Security Settings dialog box for an object, clicking the Advanced button in the Security tab, and then clicking the Edit button in the Permissions tab. It is a good habit to become familiar with the granular permissions of an object (especially one that requires increased security), although it takes more effort. Summary permissions do not always accurately reflect the state of granular permissions. For example, I have seen the total Read permission when the user actually had Read & Execute permission.
Same as Full Control Share Resolution, Full resolution Control NTFS provides owners with great options. Non-administrator users often have Full Control permission on their home directory and other files and folders. As noted, a holder of this level of rights can change the file's permissions and make himself the owner. Instead of giving users Full Control permission, you can only give them Modify permission. If the user is the owner of the file, then, if necessary, you can manually prevent him from changing permissions.
Technically, NTFS permissions are known as discretionary ACLs (DACLs). Audit permissions are known as system ACLs (SACLs). Most NTFS protected objects have both types of permissions.
Impact of Windows Trusts
By default, all Windows 2000 and later domains and forests have two-way trusts with all other domains in the forest. If a domain trusts another domain, then all users in the trusted domain have the same security permissions in the trusting domain as the Everyone group and Authenticated Users group of the trusting domain. In any domain, many permissions for these groups are assigned by default, and trusts implicitly provide broad rights that would not otherwise be granted. Keep in mind that unless the trust relationship is selective, any permissions granted to the Everyone and Authenticated Users groups are assigned to all other users in the forest.
Checking permissions from the command line
The Cacls program is described in a Microsoft article titled "". It is an older tool that has been included with Windows since the days of Windows NT. Cacls is not as useful as Subinacl or Xacls, but the utility is always available on Windows systems. You can use Cacls to view and modify files and permissions by user and group, but not create granular NTFS permissions. Currently, Cacls is limited to working with No Access, Read, Change, and Full Control permissions, which correspond to NTFS but not Share. In addition, the Read permission of Cacls corresponds to the Read & Execute permission of NTFS.
Inheritance
By default, all files, folders, and registry keys inherit permissions from the parent container. Inheritance can be enabled or disabled for individual files, folders, or registry keys, and for individual users or groups. As you can see in Figure 1, the Apply To box on the Permissions tab of the Advanced Security Settings dialog box indicates whether a particular permission is restricted by the current container, or whether it is propagated to subfolders and files. The administrator can assign permission (for individual users), which are inherited or not. V this example the Everyone group has Read & Execute permission on the current folder, and this permission is not inherited.
Figure 1: Detailed Object Resolutions
If a file or folder inherits most of its permissions, but also has a set of explicitly set permissions, then the latter always take precedence over inherited rights. For example, you can grant a user Full Control-Deny permission on the root directory of a specific volume, and have all files and folders on the drive inherit those permissions. You can then assign an access right to any file or folder on the disk, which overrides the legacy Full Control-Deny mode.
Effective Permissions
Windows Protection Monitor determines effective user permissions (the actual permissions they actually have) based on several factors. As noted above, Security Monitor first collects information about an individual user account and all groups to which it belongs, and summarizes all permissions assigned to all user and group SIDs. If Deny and Allow permissions exist at the same level, Deny usually takes precedence. If Full Control-Deny is given priority, then the user usually does not have access to the object.
By default, when considering NTFS and Share permissions (the user connects to a resource over a network), the Security Monitor should collect all Share and NTFS permissions. As a result, effective user permissions are the set of permissions granted by both Share and NTFS permissions.
For example, the user might end up with Read and Change Share permissions, and Read and Modify NTFS permissions. Effective permissions are the most limited set of permissions. In this case, the permissions are almost identical. Read and Change / Modify are effective permissions. Many administrators mistakenly believe that Read only permissions are effective because of poor, oversimplified examples or outdated documentation.
The Advanced Security Settings dialog box for Windows XP and newer has an Effective Permissions tab (see Figure 2). Unfortunately, the Effective Permissions tab only reflects NTFS permissions. The impact of Share permissions, action-based groups where the user does not have membership, and other factors such as Encrypting file system are not considered. File System- EFS). If EFS is enabled on a file or folder, then a user with the appropriate NTFS and Share permissions may be unable to access the object if they do not have EFS access to the folder or file.

Figure 2: Effective NTFS Object Permissions
It is prudent to grant Full Control permissions to regular users. It is useful to assign them the Modify permission instead. In most cases, this approach provides users with all the permissions they need, without allowing them to change rights or take ownership of themselves.
Work carefully with the Everyone group; it is better to use the Authenticated Users (or Users) group, or a special group with limited rights. An important omission of the Authenticated Users group is the lack of a Guest and an unauthenticated user.
It is not uncommon for network administrators to be asked to enter guest accounts for third-party users (eg consultants, contractors, freelance programmers). But right regular user often overkill for the guest. Create and use a group that is heavily restricted by default (for example, Full Control-Deny permission for root directories), and then explicitly allow access only to files and folders required by this guest account. Explicitly assigned permissions are preferred because they give guest users the exact permissions they need to get them to work, but no more.
Care should be taken when restricting the Everyone and Users groups, since administrators belong to these groups as well.
In the case of trusts with other domains, it is useful to use one-way and selective trust to restrict the rights of users of the trusted domain.
You should periodically audit NTFS and Share permissions to ensure that they are as limited as possible.
Using these guidelines and reference tables with brief description all permissions, you can safely go to the maze file system... The administrator can confidently assign permissions to files, folders, users and groups.
Table 1. Summary of NTFS Permissions 
Table 2. Granular NTFS Permissions 
Roger Grimes ( [email protected]) is a security consultant. Certified CPA, CISSP, CEH, CHFI, TICSA and MCSE: Security.
Laboratory work No. 2
Topic: Using techniques for working with the NTFS file system. Assigning access permissions to files and folders.
Lead time:2 hours
Target : Learn to set NTFS permissions for files and folders for individual users and groups in the operating room Windows systems 7, as well as troubleshoot resource access issues.
Theoretical information
General information about using NTFS permissions
NTFS permissions allow you to explicitly specify which users and groups have access to files and folders and what operations they are allowed to perform on the contents of those files or folders. NTFS permissions apply only to volumes formatted using the NTFS file system. They are not available for volumes using FAT or FAT32 file systems. NTFS security is effective regardless of whether the user is accessing a file or folder located on the local computer or on the network.
Folders have different permissions than files. Administrators, file or folder owners, and users with Full Control permission have the right to assign NTFS permissions to users and groups to control access to those files and folders. Access Control List
NTFS stores access control list (access control list - ACL) for each file and folder on the NTFS volume. This list lists the users and groups that have file or folder permissions set, as well as the assigned permissions themselves. For a user to access a resource, there must be an entry in the ACL called access control list item (access control entry - ACE) for this user or group to which it belongs. This entry will assign the requested access type (for example, Reading) to the user. If the ACL does not have a matching ACE, then the user will not be able to access the resource.
Multiple NTFS Permissions
You can set multiple permissions for a user and all groups of which he is a member. To do this, you must have an understanding of the rules and priorities by which multiple permissions are assigned and merged in NTFS, and the inheritance of NTFS permissions.
Effective permissions. Effective user permissions for a resource is the collection of NTFS permissions that you assign to an individual user and all groups to which they belong. If a user has Read permission on a folder and is a member of a group that has Write permission on the same folder, then that user has both permissions.
Setting NTFS Permissions and Special Permissions
You must follow certain guidelines when setting NTFS permissions. Set permissions according to the needs of groups and users, which includes allowing or preventing subfolders and files contained in the parent folder from inheriting permissions from the parent folder.
If you spend a little time planning your NTFS permissions and follow a few principles in planning, you will find that permissions are easy to manage.
To simplify the administration process, group files into folders of the following types: application folders, data folders, personal folders. Centralize public and private folders on a separate volume that does not contain operating system files or other applications. By doing so, you will receive the following benefits:
You will be able to set permissions only for folders, not for individual files;
Simplify the process Reserve copy because you don't have to back up your app files, and all your public and private folders are in one place.
· Set only the required access level for users. If you need to read a file, give the user Read permission for that file. This will reduce the chances of a user accidentally modifying the file or deleting important documents and application files.
· Create groups according to the type of access required by the group members, then set the appropriate group permissions. Assign permissions individual users only when necessary.
When setting permissions to work with data or application files, set the Read and Execute permission for the User groups. supporters and Administrators. This will prevent viruses or users from accidentally deleting application files or damaging them.
· When setting permissions for public data folders, assign Read / Execute and Write permissions to the Users group and Full Control permission to the Creator Owner group. By default, the user who created the document is also the owner of the document. The owner of a file can give another user permission to own the file. The user who accepts such rights, in this case, becomes the owner of the file. If you set the Read and Execute and Write permission to the Users group and the Full Control permission to the Creator Owner group, then users will be able to read and modify documents created by other users, as well as read, modify, and delete files and folders that they create.
File system(eng. file system) - regulations that determine the way of organizing, storing and naming data on storage media. It defines the format of physical storage of information, which is usually grouped in the form of files. The specific file system determines the size of the file name, the maximum possible file size, and a set of file attributes. Some file systems provide service capabilities, such as access control or file encryption.
File systems:
- FAT ( File Allocation Table) - the file system used by Dos and Windows
- NTFS (from the English. New Technology File System- "file system new technology") - standard file system for the family of operating systems WindowsXP, 2003
NTFS 5.0 features:
· The mechanism of permissions for access to files and folders. Provides a flexible system of restrictions for users and groups.
· Compression of files and folders. Built-in data compression helps to save disk space, while all procedures are performed transparently to the user.
· Data encryption. Encrypting File System (EPS, Encrypting File System) ensures the confidentiality of stored information, and in Windows Server 2003 eliminated some of the "information leakage" overhead of this mechanism.
· Disk quotas. You can limit the space occupied on a volume by individual users.
· Reparse points mechanism. Allows, in particular, to implement junction points, with the help of which target folder(disk) is mapped to an empty folder (called mounting a disk) under the NTFS 5.0 file system namespace on the local computer. The target folder can be any valid windows path Server 2003.
· Distributed tracking of links to files. This mechanism allows you to maintain an up-to-date link to a file, even if it has been renamed or moved to a different volume located on the same computer or on another computer within the domain.
· Sparse files. NTFS efficiently stores such files containing a large number of consecutive empty bytes.
· Change log(change journal), which logs all file and volume access operations.
The center of the NTFS file system is a file called master file table(Master File Table, MFT). It is created when the volume is formatted for NTFS. The MFT consists of a 1KB array of records. Each entry identifies one file located on disk. NTFS estimates the file size, if it is not more than 1 KB, it is stored in the MFT record.
When formatting, disk volumes are partitioned into clusters Is the minimum disk space allocated for files.
To be able to change the permissions for files and folders, select in the main Explorer menu: Tools -> Folder Options... In the window that appears, uncheck Use simple general access .
To change access rights, select in the context menu above the file or folder, select Sharing and security and go to the tab Security.
Here you can specify the rights of each user or group to read, write, execute this file or folder.
Access rights can be changed by the owner of the file, which can be seen by clicking Additionally and selecting the tab Owner... Any administrator can make himself the owner of a file or folder.

To encrypt or compress a file or folder, select from the context menu above it Properties-> Others.
Be careful with encryption, if the system is reinstalled, the encrypted files will be lost.
Tasks:
1. Create a Secret folder on the D: drive and close access to it to everyone except yourself.
2. Create a Library folder and allow everyone read-only (not write).
3. Find large file.doc format, compress it using NTFS properties, how much less space it now takes on disk, compare with compression in .zip
4. Encrypt the same file (what do you have to do to do this?), Check its unavailability under a different user.
5. Can I compress an encrypted file using .zip?
6. Create a temporary user, set a password, encrypt the file under this user, then, under the administrator's name, reset the password for this user, will the encrypted file be available?
7. Connect one of the drives as a folder to another drive, and remove the letter from this drive (i.e. so that it is visible only as a folder)
9. …
Registry, tweakers.
Source: ru.wikipedia.org
Windows Registry- database of parameters and settings of the operating room Microsoft systems Windows. The registry contains information and settings for hardware, software, users, presets. For any changes in the Control Panel, file associations, system policies, installed software, all these changes are recorded in the registry. The operation of the operating system is impossible without the registry.
The Windows Registry was introduced to organize the information previously stored in the many INI files that were used to store settings before the registry existed.
The registry is located in several files (sam, security, software, system) in the folder % SystemRoot% \ System32 \ Config, and in the folder of computer user profiles ( Ntuser.dat). To modify the registry, use Registry editor: Start -> Run -> regedit.
Remember that the editor does not check the correctness of the parameters, therefore, even with a typo, any change will be saved, which can lead to undesirable consequences. The registry itself will not recover, and the operating system may refuse to boot.
For this reason, first of all, do backup registry or the key that you are going to change. To do this, on the registry branch (section), right-click and select Export, this branch will be saved in a text file of the format .reg... Subsequently, it can be imported into the registry - double click on this file or the right button and Merge.
The Windows XP and Windows 2003 registry contains the following sections (or subtrees or hives):
· HKEY_CLASSES_ROOT- This section contains information about file extensions and programs that correspond to these extensions. It also contains information required for COM and OLE technologies to work. Some data related to the above is contained in the key HKEY_LOCAL_MACHINE \ Software \ Classes
· HKEY_CURRENT_USER- Here is information that concerns the currently active user
· HKEY_LOCAL_MACHINE- The section contains information about the configuration of the computer and how the start and stop of the services and equipment installed in the system will be handled. It also contains information related to SAM (Security Accounts Manager) and security policies. This branch is the most heavily used by applications.
· HKEY_USERS- The section contains data about computer users. Each user is assigned a specific entry, the name of which corresponds to the SID given user
· HKEY_CURRENT_CONFIG- This branch is linked to subkeys in HKEY_LOCAL_MACHINE \ System \ CurrentControlSet \ Hardware Profiles \ Current. This section contains information that is specific to hardware and is used during the preboot process to resolve interconnections for specific hardware.
Tweaker- program fine tuning and optimization of operating systems of the Windows family. Used as a replacement Registry Editor Windows. Advantages: the presence of a description of the registry keys, the presence of a search and the ability to 'roll back' changes. Disadvantages: Undocumented features are sometimes used, Microsoft does not recommend users to edit the registry.
Tasks:
10. Using the Registry Editor
a)Change registry keys to use ClearType anti-aliasing on the welcome screen, change the screensaver that appears on the welcome screen
b)Find and export registration information for a Nero (or other) program
11. Using Tweaker (like NeoTweaker)
a)Do not show arrows on desktop icons
b)Try active window mode (x-mouse, like in unix) - the window becomes active when you hover over it with the mouse pointer, without additional clicking
c)Disable CD autoplay (autoplay may be unsafe)
d)Disable built-in CD burning function
e)Change html code editor in Internet Explorer from Notepad to DreamWeaver
f)Make the tooltip above the clock show the day of the week, not just the date
g)Make sure to show the commands executed when the computer boots and shutdown - this will help you find out what the system is spending a lot of time on.
h)Set the delay for the appearance of the menu 100ms instead of 400ms
i)Disable Manager QoS packages(will speed up the network by 20%)
j)Change the percentage of free hard disk space at which the system will warn about insufficient disk space
k)Disable sending error reports to Microsoft (for security reasons, to save bandwidth and not to get bored with questions after a program freezes)
l)Enable automatic appending of paths to command line by the Tab key (i.e. instead of a long path, you can write the first characters and press Tab)
m)Make NumLock Enabled at Boot
n)…
Service.
Source: computerra.ru, oszone.net
Service Microsoft Windows is an application that runs in the background. Some services start automatically when the computer boots, others only when certain events occur. As a rule, services do not have user interface... Services are used to provide functionality that runs over a long period of time and does not require user intervention on the computer. Services can run under the security context of an account other than the current user account or the default account.
During Windows work XP has many services running, but not all of them are useful for normal work your computer. To view the list of running services, do the following:
· Start - Run - cmd – net start - list of running services,
- or Start - Run - cmd – services.msc,
- or Start - Administrative Tools - Services
| Table 1. Windows 2000 / XP / 2003 Server Services | ||
| Service name | Service Description | Shutdown option |
| Bluetooth Support Service | Supports Bluetooth devices installed on the computer and discovers other devices in range | Turn off if you are not using devices that connect to your PC via Bluetooth |
| DHCP client | Manages network configuration by registering and updating IP addresses and DNS names | |
| DNS client | Allows for this computer DNS names in addresses and caches them. If the service is stopped, it will not be able to resolve DNS names and host the Active Directory domain controllers | If the network is not in use, you can painlessly turn it off |
| Fax | Allows you to send and receive faxes using the resources of this computer and network resources | If we do not use this function, then safely turn it off |
| MS Software Shadow Copy Provider | Manages shadow copies obtained by volume shadow copy | In most cases, you can turn off |
| QoS RSVP | Provides network notification and management local traffic for QoS programs and control programs | Along with disabling the traffic reservation, QoS completely disables the QoS channel reservation. Switch off |
| NetMeeting Remote Desktop Sharing | Allows verified users to access the work Windows desktop over the corporate intranet using NetMeeting. If this service is stopped, remote control desktop is not available | It is unlikely that someone wants to entrust the management of their PC to someone else. Let's add to this the potential danger of unauthorized entry into the system and conclude - turn off |
| Telnet | Allows a remote user to log in and run programs, supports a variety of TCP / IP Telnet clients, including computers with operating systems Unix and Windows. If this service is stopped, the remote user will not be able to run programs | If this function is not used, be sure to turn it off, otherwise there is a danger of unauthorized entry into the system. |
| Automatic update | Download and install Windows updates... If the service is disabled, then this computer will not be able to use the features automatic update or website Windows Update | Disable as any updates can always be done manually |
| WMI performance adapter | Provides information about performance libraries from WMI HiPerf providers | In most cases, it can be turned off, although, perhaps, someone may need |
| Wireless setting | Provides automatic tuning 802.11 adapters | If we do not use Wi-Fi, then turn off |
| Windows Firewall / Internet Access Sharing (ICS) | Provides support for address translation, addressing, and name resolution services, or prevents service intrusion into home network or small office network | If you are using FireWall third party manufacturer and your PC is not an Internet gateway for another PC on the network, then feel free to turn off |
| Secondary login | Allows you to run processes as a different user. If the service is stopped, this type of user registration is not available | Disable, otherwise this service may cause unauthorized access to the system |
| Auto connection manager remote access | Creates a connection to a remote network when a program accesses a remote DNS or NetBIOS name or address | It is used very rarely, so you can safely turn it off |
| Remote Desktop Help Session Manager | Manages remote assistance capabilities. After stopping the service, Remote Assistance will be unavailable | Creates a potential threat of penetration into the system, and the help from it is questionable. Switch off |
| Network DDE Manager | Manages dynamic data exchange (DDE) network shares. If the service is stopped, DDE network shares will not be available | |
| Print spooler | Loads files into memory for later printing | No printer - turn off |
| Performance Logs and Alerts | Controls the collection of performance data from local or remote computers. Collecting is performed on a scheduled basis and ensures that this data is written to logs or triggers an alert | In most situations, recording performance data will not be required. Calmly turn off |
| A source uninterruptible power supply | Manages uninterruptible power supplies connected to the computer. | No UPS, turn off |
| Distributed Transaction Coordinator | Coordination of transactions that span multiple resource managers such as databases, message queues, and file systems. If the service is stopped, no transactions will be executed | If the PC is not a server that uses databases, you can safely turn off |
| NetBIOS over TCP / IP Helper | Includes support for NetBIOS over TCP / IP (NetBT) service and NetBIOS name-to-address resolution | If for some reason you need NetBIOS support over TCP / IP, we do not touch this service. But in most cases, you can safely turn it off. |
| Infrared communication monitor | Supports IrDA devices installed on the computer and detects other devices in range | If you are not using devices that connect to your PC using infrared communication, turn off |
| Computer Browser | Serves a list of computers on the network and issues it to programs upon request. If the service is stopped, the list will not be created or updated | If the network is not in use, then turn it off, although, in general, it is enough to leave it turned on on one PC in your network |
| Task Scheduler | Allows you to configure a schedule for the automatic execution of tasks on this computer. If the service is stopped, these tasks cannot be started at the scheduled time | If you are not keen to run programs automatically in set time then turn off |
| Server | Shares files, printers, and named pipes for this computer through network connection... If the service is stopped, these functions will fail | If the network is not in use, you can painlessly turn off |
| Windows Time Service | Manages the synchronization of date and time across all clients and servers on the network. If the service is stopped, date and time synchronization will be unavailable | If the network is not in use, then turn it off, although if there is a network, turning off this service in most cases will not hurt |
| SSDP Discovery Service | Enable discovery of UPnP devices on your home network | If the network is not in use, then turn it off, and even if there is a network, it is rarely needed |
| Help & Support | Enables the Help and Support Center to run on this computer. If the service is stopped, the help and support center will be unavailable | Disable, since there is no sense in this support ... Although if you cannot do without this service, you can leave it on |
| Network DDE Service | Provides network transport and security for dynamic data exchange (DDE) in programs running on one or more computers. If the service is stopped, network transport and DDE security will be unavailable | If the network is not in use, you can painlessly turn off |
| Remote registry | Allows remote users to modify registry settings on this computer. If the service is stopped, the registry can only be modified by local users running on this computer | It is unlikely that anyone would want to entrust the management of their registry to someone else. Let's add here the potential danger of unauthorized entry into the system and conclude: turn off |
| Terminal Service | Provides the ability for multiple users to interactively connect to a computer and displays the desktop and applications on remote computers. Provides the foundation for Remote Desktop (including Remote Administration), Fast User Switching, Remote Assistance, and Terminal Services | If the network is not in use, it can be turned off painlessly. And if you have a network, think carefully, do you need someone other than you to have access to your PC? |
| System Restore Service | Performs system recovery functions. To stop the service, you must turn off System Restore in the System Restore tab of the computer properties | If you do not need to roll back the system by a certain date, then turn it off, because the service requires a lot of hard disk space. True, I did not do this, because sometimes, in case of errors that happened through my fault, I had to roll back the system |
| Error Logging Service | Allows error logging for services and applications running in a non-standard environment | A useless service for most users. Switch off |
| Network login | Supports pass-through authentication of account logon events for domain computers | If the network is not used or a network without domains, then turn off |
| Network Location Service (NLA) | Collects and stores location information and network settings and notifies applications when they change | If the network is not in use, you can painlessly turn off |
| Messaging service | Sends and receives messages submitted by administrators or notification service. Not related to MSN Messenger. If the service is stopped, no alert will be sent | If the network is not in use, you can painlessly turn off |
| System Event Notification | Logs system events on the network (such as logging into Windows) and changes in power supply. Notifies COM + system event subscribers by sending notifications | You can safely turn it off. This service is rarely needed |
| Fast User Switching Compatibility | Management of applications that require support in a multi-user environment | Disable in most cases, as there are very few programs that use this service. True, there is one "but": if you want to work under your account without interrupting the processes of another account, this service cannot be turned off |
| Smart cards | Controls access to smart card readers. If the service is stopped, the computer will not be able to read smart cards | If you are not using smart cards, turn off |
| Image Download Service (WIA) | Provides services for obtaining images from scanners and digital cameras | If the scanner and digital camera not used on this PC, turn off |
Tasks:
1. Configure what is known as a 'gaming' service configuration, where all but essential services are disabled to ensure maximum performance on your computer.
3. Enable services responsible for running local network and the Internet.
4. …
Drivers, directX.
This article ideologically continues the article. As it was said in it, after selecting users and (or) groups, you must specify the parameters for accessing them. You can do this by using the NTFS file system permissions, which are discussed in the following table.
File permissions
- Reading. You are allowed to read the file, as well as view its parameters, such as owner name, permissions, and additional properties.
- Recording. Allowed to overwrite the file, change its parameters, view the name of its owner and permissions.
- Reading and Execution. Read permission and right to run the executable application.
- The change. Allowed to modify and delete the file, as well as anything provided by the permissions Read and Execute, and Write.
- Full access.
- Full file access allowed. This means that all actions provided for by all of the above permissions are allowed. You can also take ownership of the file and change its permissions.
Folder permissions
- Reading. You are allowed to view subfolders and files, as well as their properties, such as owner name, permissions, and read-only attributes such as Read-only, Hidden, Archive, and System.
- Recording. It is allowed to create and place new files and subfolders inside the folder, as well as change the folder settings and view its properties, in particular the owner name and access permissions.
- List of folder contents. You are allowed to view the names of files and subfolders contained in the folder.
- Reading and Execution. Files in subfolders are allowed to be accessed even if there is no access to the folder itself. In addition, the same actions are allowed as for the Read and List folder contents permissions.
- The change. All actions for the Read and Read and Execute permissions are allowed, and the folder can be deleted.
- Full access. Full access to the folder is allowed. In other words, all actions provided for by all of the above permissions are allowed. Additionally, it is allowed to take ownership of the folder and change its permissions.
- Special Permissions. A set of additional permissions that differ from the standard ones.
The creator of the file is always considered to be its owner, who has the rights Full access, even if Account owner is not listed on the tab File security... In addition to the above file permissions, you can select two additional types of permissions.
- Change of owner... This type of permission allows the user to take ownership of the file. This type default permissions assigned to group Administrators.
- Change permissions... The user gets the ability to change the list of users and groups who have access to the file, as well as change the types of access permissions to the file.