You use your Android smartphone (tablet) to save personal photos, read important emails, make online purchases with your credit card, editing and transferring important documents? If your answer is yes, then you should consider encrypting your device.
Unlike the iPhone, Android devices They do not automatically encrypt the data that is stored on them, even if you use a password to unlock the device, but if you are using Android Gingerbread 2.3.4 or higher, then encryption is easy to enable.
Encrypting your phone means that if your phone is locked, your files are encrypted. Any files sent to and received from your phone will not be encrypted unless you use additional methods.
The only difference between an unencrypted and an encrypted phone from the user's point of view is that you will now have to use a password to unlock the phone (tablet).
If your phone is not encrypted then the password is just a screen lock. In fact, in this case, the password simply locks the screen - that is, it does nothing to protect the files that are stored on the device. So, if attackers find a way to bypass the lock screen, then they get full access to your files.
In case the phone is encrypted, the password is the key that decrypts the encrypted files.
That is, when the phone is locked, all data is encrypted, and even if attackers find a way to bypass the lock screen, all they find is encrypted data.
How do I enable encryption on an Android device?
1. Open the Settings menu.
2. In Settings, select Security> Encryption (Encrypt device).
3. As required, you must enter a password of at least six characters, at least one of which is a number.

As soon as you set the password, the process of encrypting your files will start. Encryption can take an hour or more, so you must turn on the charger before encrypting it.
Once the encryption process is complete, you're done! Make sure to save your password in a safe place as it will come in handy every time you want to access your phone. Please note that if you forget your password, there is currently no way to recover it.
In fact, encrypting Android devices, along with the obvious advantages, also has significant disadvantages:
- Imagine that every time you want to call, you need to type a complex password. I wonder how soon you get tired of this?
- You will not be able to decrypt an encrypted device, it is simply not provided. There is only one way to decrypt - reset the phone to factory settings. In this case, of course, all your data will be lost. It will look especially interesting if you forget to do it first. backup.
Thus, today there is a difficult choice - either you encrypt your device and put up with huge inconveniences, or you get usability, but at the expense of security. Which path will you choose? I do not know. Which path would I choose? I can't answer either. I just do not know.
Vladimir BEZMALY , MVP Consumer Security, Microsoft Security Trusted Advisor
For improved privacy and data protection, people concerned about this issue can use encryption of information that is stored on their mobile device using the function built into the Android operating system.
A number of caveats should be made when applying this method. This process is one-way, that is, when it is turned on, there is no way to turn it off without consequences, since the encryption mechanism is turned off by resetting the mobile device to factory settings. Before starting encryption, it is recommended to make backup copies of data, and in no case should you interrupt the encryption process, otherwise the owner of a smartphone or tablet will face irreversible consequences associated with the loss of information, and there is also a risk of completely “killing” the device. Before the encryption process, you should also make sure that you have set an alphanumeric password or PIN, which is used to unlock the screen, as the operating system will use it as the decryption key. 
What is the encryption process on Android
To start the encryption process, you need to go to System Settings - Security - Encrypt device. After data encryption, you will need to enter the preset alphanumeric password or PIN each time the phone boots up. If necessary, it is possible to encrypt not the entire device, but only selected files and directories. In such cases, the SSE Universal Encription application is perfect, which includes all popular encryption algorithms, including Blowfish-256, AES-256, and Sarpent-256. The application also includes three modules: Password Vault, for safe storage passwords in various folders, Message Encryptor, which allows you to encrypt both whole text and its fragments, and, as a more interesting and useful module is File / Dir Encryptor, which allows you to select both individual files and directories through the built-in browser window , which, subsequently, are securely encrypted according to the algorithm selected by the user. You can download the application from Google Play or via a computer.
MagaZilla online product catalog provides the ability to compare products and stores. If you need a computer mouse, prices on the site http://m.ua/ available to every visitor. Come in and familiarize yourself with the catalog of companies where you can buy goods.
Also for better data protection on mobile devices you can use the Cyanogen Mod, which can only be installed using a computer with an operating Windows system... Instead of Cyanogen Mod, you can also install the Replicant distribution, which is based on Cyanogen Mod, but is free and open source and replaces all proprietary Android device drivers with alternative open source drivers.
Modern gadgets have long become a tidbit for all sorts of scammers and other intruders, but few of ordinary users thinks about protecting their devices and data on them. Someone considers protection unnecessary, because, in their opinion, they have nothing of value and have nothing to hide. But below I will describe why this position is erroneous and why you should think about protecting your personal data by activating device encryption right now.
Attackers can harm you
Your data is not only your photos and videos, but also records in toys. It is also the contacts of your friends and colleagues, data in the text of messages that you, your friends or colleagues send to each other. Any piece of information can be useful to intruders and, with their help, they can seriously harm you.
For example, they may steal a very personal picture from your device and demand a ransom, threatening to send it to your work colleagues or relatives. Of course, if you are not a celebrity, then he is unlikely to get on the network and become public, there you are not interesting to anyone. But who said that you can't make money on this? In one case, it can ruin a career, in another, it can destroy a family.
Of course, you shouldn't store such pictures on your device anyway, but this is just an example. But you can do something similar with any other, at first glance, more harmless information. For example, with text messages.
Do not neglect the security of your data, which at first glance may seem to you useless to someone, because they can still cause serious harm.
Attackers can harm your loved ones
Given the points described above, do not underestimate attackers. They can use the contact information of your friends, colleagues and relatives to obtain some information from them on your behalf or somehow illegally use their personal information obtained from private messages to you. By doing so, they can also set you up. All this can lead to very serious consequences for them, and the reason for this may be the article, a negligent attitude towards the security of their personal data.
After a reset, the data can be recovered
You might think that a reset to delete all data from your phone would be enough at the time of sale, but in reality it is not. Data can be recovered if it has not been encrypted. Thus, if an attacker acquires a previously unencrypted phone from you, on which the reset was carried out, he will gain access to your data. And at the same time it can harm you or your loved ones, as described in the two paragraphs above. Better to enable encryption to prevent this
Enabling encryption is easy
Many people think that encryption will slow down the device and that it is not easy to activate it. Fortunately, this is not the case. Encryption is activated in the settings in the security section and the device works exactly the same as before, no problems arise when using it. Therefore, you should not postpone safety for the sake of some myths.
Smartphones have firmly taken their place in our lives. We trust them with our personal data, sometimes very confidential, without thinking about the cases when the device falls into the wrong hands. Sometimes this shortsightedness can lead to disaster. At the moment, smartphones based on the Android platform are leading in terms of the number of sales worldwide. The advantages of Android are the use of open technologies, ease of use, and the ability to encrypt data.
Becoming the proud owner of a smartphone on Android base, I began to wonder how much securely smartphone encrypts my data? I devoted several October evenings and this article to this fascinating topic. For clarity, I presented in a graphical form the architecture of the Cryptfs module and the Android encryption algorithm.
Android encryption security
Full disk encryption allows you to maximally secure your data on Android devices. Data encryption was added in Android 3.0 Honeycomb, and this version of Android was geared towards tablets. For the first time for smartphone owners, the encryption feature appeared in version 4.0. The mechanisms for implementing the data encryption system will be considered on the example of new versions of Android.
Full disk encryption protects sensitive data in the event of device loss, theft or confiscation for any reason. For intelligence officers, obtaining data on encrypted devices is very difficult and depends on a number of conditions. If the device was turned off during transportation, or if the battery was simply discharged, then the process of obtaining data becomes more difficult. The fact is that full encryption is vulnerable to a cold boot attack, with the help of which it is possible to read information from random access memory... This is achieved due to the fact that when the power is lost, the RAM is cleared for a certain amount of time, and when freezing, the clearing process slows down and can last from several seconds to several minutes. AES keys can be extracted from the RAM of Android devices, but disk decryption is only possible with an unlocked bootloader. You can resort to the procedure for unlocking the bootloader only if unlocking does not lead to the destruction of all user data (which depends on specific model device). But even if the bootloader is locked, it is possible to extract contact lists, visited websites, photos, etc. from RAM. For the first time, this type of attack on smartphones was demonstrated by German researchers who called their method FROST. They demonstrated an attack on Samsung Galaxy Nexus, however on smartphone Samsung Galaxy SII, they were unable to decrypt the drive, they explained this by the fact that encryption on this device differs from encryption in the official Android release.
In short: If you use a pattern to access the phone, then 99% of this is enough for no one without your knowledge to be able to access the information on the phone. If the data on the phone is very sensitive, then the built-in full encryption of the phone should be used.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and use special means to protect your phone from unauthorized access if it is stolen or lost.
- Who should protect your phone data from.
- Built-in data protection in Android.
- Full Phone Memory Encryption
- Outcomes
What information is stored on the phone and why should it be protected?
A smartphone or tablet often acts as a mobile secretary, freeing the owner's head from storing a large amount important information... The phone book contains the numbers of friends, employees, family members. In the notebook, they often write credit card numbers, access codes to them, passwords to social networks, e-mail and payment systems.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen on purpose to infiltrate personal life or share the profit with the owner.
Sometimes they are not stolen at all, and they are used for a short time, unnoticed, but a few minutes is quite enough for an experienced attacker user to find out all the details.
Loss of confidential information can turn into financial ruin, personal ruin, family breakdown.
I wish I didn't have it! - the former owner will say. - How good that you had it! - the attacker will say.
And so you need to protect on your phone:
- Accounts. This includes, for example, access to your mail mailbox gmail... If you have set up sync with facebook, dropbox, twitter. Logins and passwords for these systems are stored in clear text in the phone profile folder /data/system/accounts.db.
- History of SMS-correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that Web Browser(built-in or third-party) remembers all passwords and logins for you. All this is stored in open form in the program profile folder in the phone memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to the account open, even if you did not specify to remember the password.
If you are using sync mobile browser(Chrome, FireFox, Maxthon, etc.) with a desktop version of the browser for transferring bookmarks and passwords between devices, then you can assume that you can access all passwords from other sites from your phone. - Memory card. If you store confidential files on the memory card or download documents from the Internet. Typically, the memory card stores photos and videos.
- Photo album.
Who should protect phone data from:
- From a random person who finds your lost phonel because from “accidental” phone theft.
It is unlikely that the data in the phone will be of value to the new owner in this case. Therefore, even simple protection with a graphic key will ensure the safety of data. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers / children / wives), who can access the phone without your knowledge, taking advantage of your absence. Simple protection will keep your data safe.
- Granting access under duress
It happens that you are voluntarily forced to provide a phone and open access to the system (information). For example, when your wife, a government official, or an employee asks you to look at your phone service center where did you take the phone for repair. In this case, any protection is useless. Although it is possible, with the help of additional programs, to hide the fact of the presence of some information: hide part of SMS correspondence, part of contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protections on Android devices .
1. Lock screen with Pattern.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, then no one can use it. But if you deliberately fell into the wrong hands for your phone, then it is unlikely to save. Hacking can even happen at the hardware level.
The screen can be locked with a password, PIN and Pattern. You can choose a blocking method by running the settings and selecting the Security -> Screen lock section.
Graphic Key(Pattern) - c The most convenient and at the same time reliable way to protect your phone.

None- lack of protection,
Slide- to unlock, you need to slide your finger across the screen in a certain direction.
Pattern- this is the Graphic Key, it looks something like this:
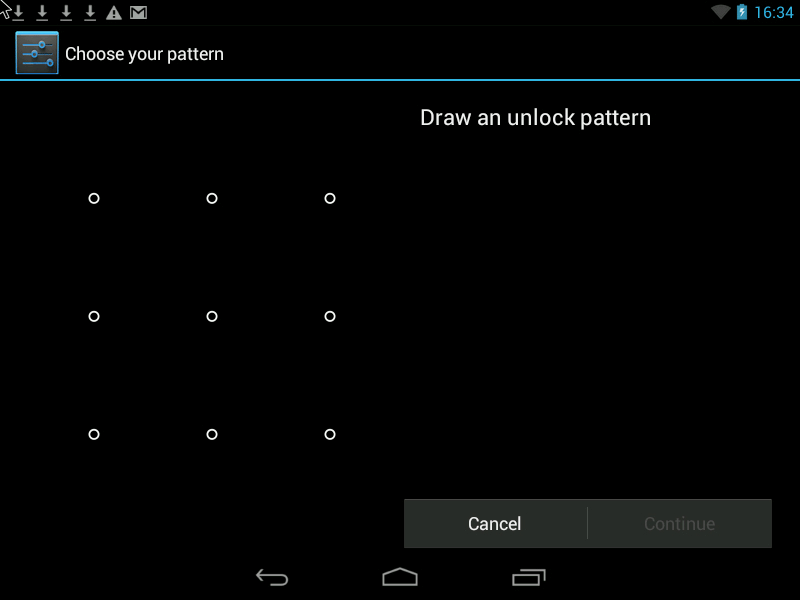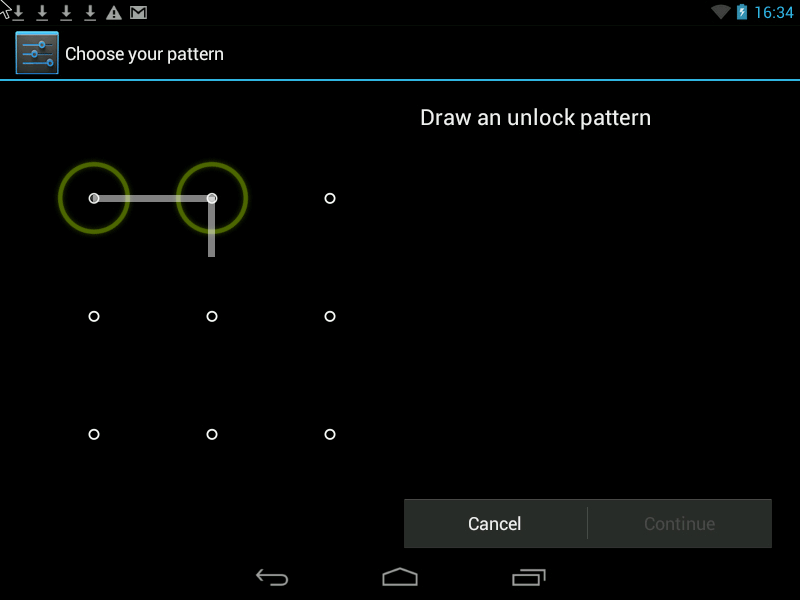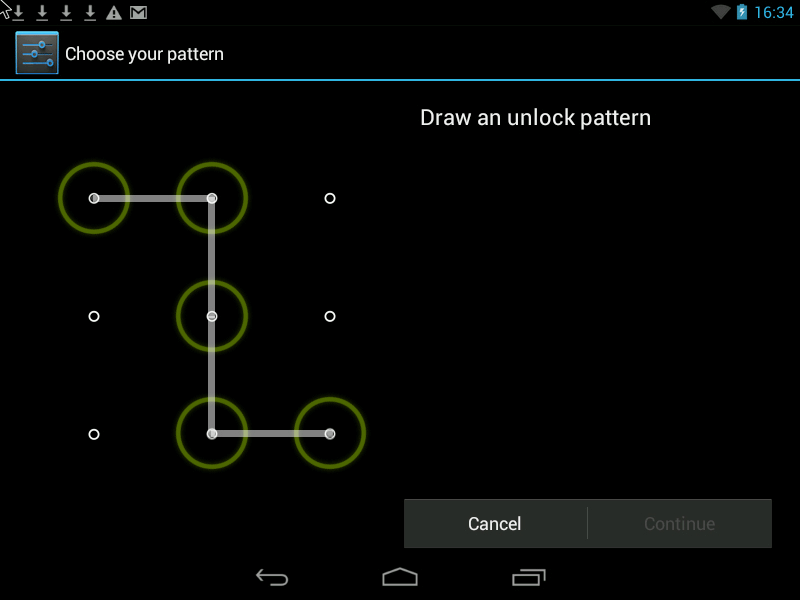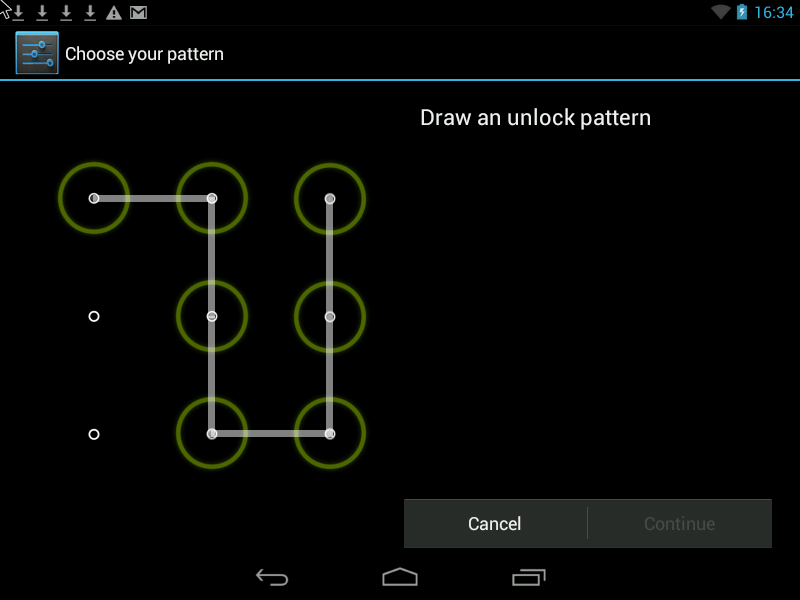
There are two ways to improve security.
1. Increase the input field of the Pattern key. It can vary from 3x3 pixels on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of points and the "path" of the pattern on the smartphone screen so that it is impossible to peep the key.
3. Set automatic screen lock after 1 minute of inactivity of the phone.
Attention!!! What happens if you forget your pattern:
- The number of incorrect attempts to draw a Pattern is limited to 5 times (in different phone models, the number of attempts can be up to 10 times).
- After you have tried all your attempts, but still have not drawn the Pattern Key correctly, the phone is locked for 30 seconds. After that, you will most likely have a couple of tries again depending on your phone model and Android version.
- Next, the phone asks for the login and password of your Gmail account, which is registered in the phone's Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It so happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN Is a password consisting of several numbers.
Finally, Password- the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Phone memory encryption.
Feature included in the package Android version 4.0 * and higher. for tablets. But this feature may not be available on many budget phones.
It allows you to encrypt the internal memory of the phone so that it can be accessed only by a password or PIN-code. Encryption helps protect information on your phone in the event c
targeted theft. Attackers will not be able to gain access to your data from the phone in any way.
A prerequisite for using encryption is to set up a screen lock with a password.
This method is used to save user data located in the phone's memory, for example, the phone book, browser settings, passwords used on the Internet, photos and videos that the user received with the camera and did not transfer to the SD card.



- SD card encryption is enabled as a separate option.
- Encrypting memory may take up to an hour depending on the amount of memory on your device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery in this case is not provided. You can make your phone or tablet a full RESET, i.e. reinstall Android, but the user data from the phone or tablet memory will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get the phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply be absent on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have encryption function. On some phones, this function is located in the "Memory" section.
Flaws:
- You will have to constantly enter a rather complex password (6-10 characters), even if you just want to call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when the phone screen is turned on. On some phone models, the minimum password length can be 3 characters or more.
- On some phone models, it is not possible to turn off encryption if you want to opt out of entering your password permanently. Encryption is disabled only by restoring the phone to factory settings and deleting all data.
External SD card encryption
The function is included in standard package Android 4.1.1 for tablets. Absent in many budget builds.
The function provides reliable protection of data on an external SD card. Personal photographs, text files with commercial and personal information may be stored here.
Allows you to encrypt files on the SD-card without changing their names, file structure, while preserving the preview of graphic files (icons). The function requires a lock password to be set on a display with a length of at least 6 characters.




It is possible to cancel encryption. When the password is changed, it is automatically re-encrypted.
If the user has lost the memory card, the encrypted files cannot be read through the card reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet to a computer via a USB cable, the encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write any other unencrypted files to the card through the card-reader, they will also be encrypted after the card is inserted into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- The data is encrypted at the file level (the names of the files are visible, but the contents of the file are encrypted).
Disadvantage of the program:O Absence in most Android assemblies.
It should be emphasized that the best data safety is a complete copy of it on your Computer in A smartphone is a rather fragile device of small size, which means there is always a possibility of its breakage or loss.
Improving the usability of a secure smartphone
Fully encrypting your phone provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
V Android system from version 4.2 * it is possible to bring some applications \ widgets to the lock screen, and thus you can perform simple actions without permanently unlocking the phone (without entering a 6-digit password).
Outcomes:
- The built-in and free features to protect your phone are very reliable. They are able to protect from prying eyes the user's contacts, his correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone memory and on the removable SD card.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use a too complex PIN-code or password on the lock screen (the Pattern Key is not suitable), the irreversibility of encryption internal memory phone, i.e. the only way to opt out of encryption is full reset phone settings.
- Important! Make sure that in case you forgot your password or Pattern, you can restore access to the phone, or you can easily restore the phone settings and information in case you have to do a hard reset (reset the phone to factory settings with the loss of all data).
- It is only necessary to store a backup copy of confidential data on your Computer, on DVD disc or in the cloud.