Learn what to do if you forget your iCloud Security Code for iCloud Keychain Access.
If you enter the wrong iCloud Security Code too many times when using iCloud Keychain, it will be disabled for this device and the keychain in iCloud is deleted. One of the following messages may be displayed.
- “The security code has been entered unsuccessfully too many times. Verify this iPhone from one of your other devices using iCloud Keychain. If your devices are missing, reset your iCloud Keychain. "
- “Too many attempts were made to enter your iCloud Security Code. Verify this Mac from one of your other devices using iCloud Keychain. If your devices are missing, reset your iCloud Keychain. "
If used, the device is considered trusted when you sign in. You do not need to enter an iCloud Security Code to use iCloud Keychain.
If you have access to a trusted device that uses iCloud Keychain Access
You can create a new iCloud Security Code on another device that also uses iCloud Keychain.
On your iPhone, iPad, or iPod touch:
On Mac computer with OS X Yosemite or later
On a device that has iCloud Keychain turned off, create a new iCloud Keychain that contains the username, passwords, and other keychain objects on the device:
A confirmation window will open on the device on which you created the new iCloud Security Code. Approve adding a new iCloud Keychain for the device.
If you can't access a device that's using iCloud Keychain
To reset iCloud Keychain preferences:
To access Apple branded services such as iCloud, App Store, iMessage, Facetime, etc. an iOS device user needs a personal account called an Apple ID. This account consists of a login - the address is used as it e-mail, to which the identifier is tied and the password specified by the user taking into account a number of security requirements.
At first glance, it seems that such a classic login + password protection seems to be enough, but many users believe otherwise. And, in fact, there is cause for concern. Think for yourself, finding out someone's e-mail address in our time is a nonsense business - we leave it literally everywhere. The password is also not so difficult to figure out - various hacker programs that allow you to select secret codes, today there are masses.
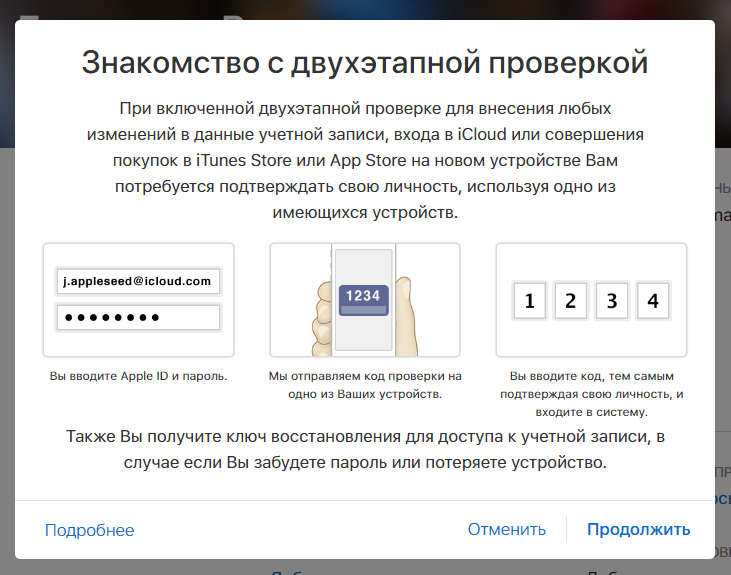
Realizing this sad situation, Apple offered the user a new type of protection: for users of old i-devices that cannot update to iOS 9 - two-step verification, for those who are lucky enough to have a younger "apple" - two-factor authentication.
In general, both methods of protection are very similar, they assume that after specifying the login and password of the identifier, the user must also enter special code... In this article, we'll explain what an Apple ID verification code is, where to enter the code, and how to enable 2-Step Verification / Two-Factor Authentication for your device.
Two-step verification
So what is two-step verification? This is an additional measure to protect access to Apple branded services - if you enable two-step verification, an attacker will not be able to log into one or another i-service, even if he knows the login and password of your personal identifier. For access, he will also need a special code.
In particular, two-step verification protects against unauthorized access to the Apple ID edit page, iMessage, FaceTime, all content purchase services, and cloud service iCloud - which is especially important, because if an attacker ends up in your "cloud", he will not only gain access to all your personal data that you back up, but can, for example, block your iOS device by turning on Lost Mode and demand money for unlocking.
How do I enable two-step verification?
To enable 2-Step Verification, follow this simple guide:
Ready! Checking is activated. Now try to go, for example, to your Personal Area on iCloud.com, after entering your username and password, you will need to specify the code sent to trusted gadgets in a special window. If the entered code does not fit, access will be denied, despite the fact that you know the username and password.
An important point! The most reliable scheme is to use a trusted person's smartphone as a trusted device, and here's why. Imagine your iPhone was stolen, your Apple ID was found out, and they were trying to log into iCloud to get certain confidential information. If you indicated the phone number of your iPhone, that is, stolen, as a trusted one, then attackers will easily receive a verification code and bypass two-step verification. If the code comes to another device, the fraudsters will first have to find out which one and steal it as well.
How do I turn off two-step verification?
If for some reason you think that such a "complex" type of access to branded services no longer suits you, you can always disable it, for this:
- Follow this link and enter your personal account for setting up Apple ID by entering your password and login of your personal account.
- Click the "Security" menu, then "Change".
- Select the "Disable two-step verification" option.
- In the next window, you will be asked to indicate your date of birth and verification questions - after you enter these parameters, you can again use only a pair of login + password to enter all i-services, but when you enter your personal Apple ID control cabinet, you will also need answer the questions asked.
Information about the successful disabling of two-step verification will come to your email.
Two-factor authentication
Like 2-Step Verification, two-factor authentication is an additional security measure for logging into Apple-branded services. Only in a situation of working with two-factor authentication, the security mechanism turns out to be more thoughtful and perfect, according to the "apple" giant.
How do I set up two-factor authentication?
As we said above, two-factor authentication is an option that is not available to all users, but only to those who own mobile i-devices with iOS 9 and later versions of the platform loaded on board. Does your gadget satisfy this requirement? Then we'll tell you how to enable authentication:
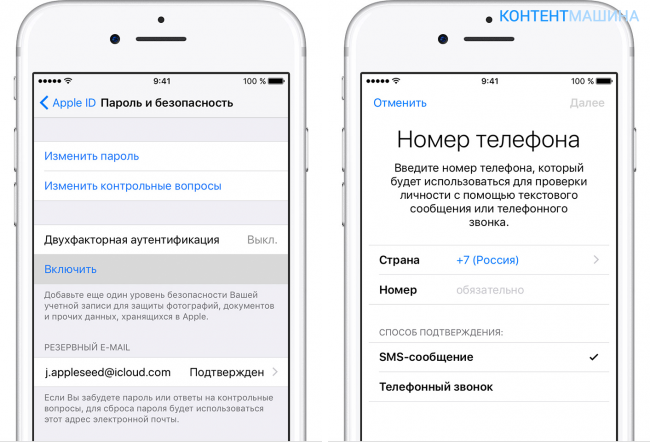
That's all! We have activated the protection, now we need to configure it:
- In the window that appears after activating authentication, enter your trusted phone number and a convenient way to send the code.
- Wait for the code to be sent to the specified number.
- Tap "Enable ...".
Ready! Protection is activated. It operates on the principle of a two-step check - when you try to enter one or another Apple service, you need to enter not only a login and a secret ID cipher, but also a special verification code.
Mac owners can activate two-factor authentication with the following simple instructions:
- Click the "Apple" menu, then " System settings"/" ICloud "/" Account ".
- Select the "Security" section, click "Enable ..."
Important! Your Mac must have OS El Capitan or a newer platform version.
How do I turn off two-factor authentication?
In general, the "apple" giant categorically does not recommend disabling protection, but if you decide to do this, you need to go to the Apple ID management page, specify your username, password and verification code, and then select "Edit" / "Disable ..." in the "Security" submenu. ".
Two-Step Verification vs. Two-Factor Authentication: Is There Any Difference?
An attentive reader could not help but have a question - if the work of the above Apple ID security systems is so similar, then what are their differences and why authentication is declared to be a more perfect mechanism for ensuring user security. Frankly speaking, there is no direct answer to this question.

Apple itself on the official support page says something like the following. Allegedly two-factor authentication is an updated security service that uses more advanced methods of setting trusted devices and sending confirmation codes, as well as optimized work in general.
That is, as you can see, the differences seem to be indicated, but nothing is clearly not clear. So it remains to trust the company and, if your device supports two-factor authentication, choose this type of protection. That being said, it is important to note that before activating of this type protection, you must first disable two-step verification, if it was enabled.
Let's summarize
Well, now you know what 2-Step Verification and 2-Factor Authentication are and how to enable and manage these options. In addition, you understand the importance of activating these protection mechanisms. You can read more about two-step verification and two-factor authentication in the "Support" section of the Apple website.
It marked the emergence of another great service within iCloud for users of Apple technology - password synchronization using iCloud Keychain. Apple has gone to great lengths to make it easy to set up and use this feature, but our readers still have a lot of questions about this new product.
What can iCloud Keychain do?
ICloud Keychain offers:
- sync logins, passwords and data from Safari forms
- sync credit card data
- sync Wi-Fi passwords
Synchronization works on Macs running OS X 10.9, iPhone, iPod touch, and iPad running iOS 7.0.3. When you activate a keychain in iCloud, a single cloud storage which collects ALL of your passwords. All of them are simultaneously available from all your devices connected to the same iCloud account.
Please note - iCloud Keychain only works with Safari on Macs! For Chrome, Firefox or Opera users new function Apple is of little use, because there are no plugins for these browsers that add support for these browsers. There are no alternatives to Safari on iOS in this case either.
Setting up iCloud Keychain on Mac for the first time
Let's say right away - for residents of Ukraine, Belarus and other CIS countries not listed in this list, activating Keychain Access from Mac is the only way to properly configure this function.
Open Mac settings, go to the iCloud remote, turn on the "Keychain Access" checkbox:
Mac insistently prompts you to enable the password request from the user account immediately after waking up from sleep or unlocking the screen - of course, for added security. This suggestion can be ignored.
You will then be asked to create a Keychain PIN. By default, this is a four-digit number that you need to remember and enter when connecting each new device to your Keychain:

But this is not necessary either. Pay attention to the "Advanced" button. It opens several options regarding the PIN:
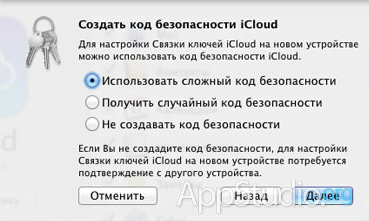
The first will allow the paranoid to set a code of any length using any characters, not just numbers. The second will generate the code automatically. The third will allow you to refuse the security code altogether. But how will the confirmation of new devices take place in this case? It's very simple - with the help of your other devices.
After creating a PIN-code or canceling it, the setup will be completed.
The initial setup of Keychain on iOS is similar - go to the "Settings-iCloud" menu and enable the "Keychain" checkbox, and then create a PIN. The problem is that you will be forced to enter the number mobile phone, and only Russia is supported from the CIS countries.
Now let's talk about connecting new devices to iCloud Keychain.
Connect a new iOS device to iCloud Keychain
Go to the "Settings-iCloud" menu already mentioned above and select "Keychain":
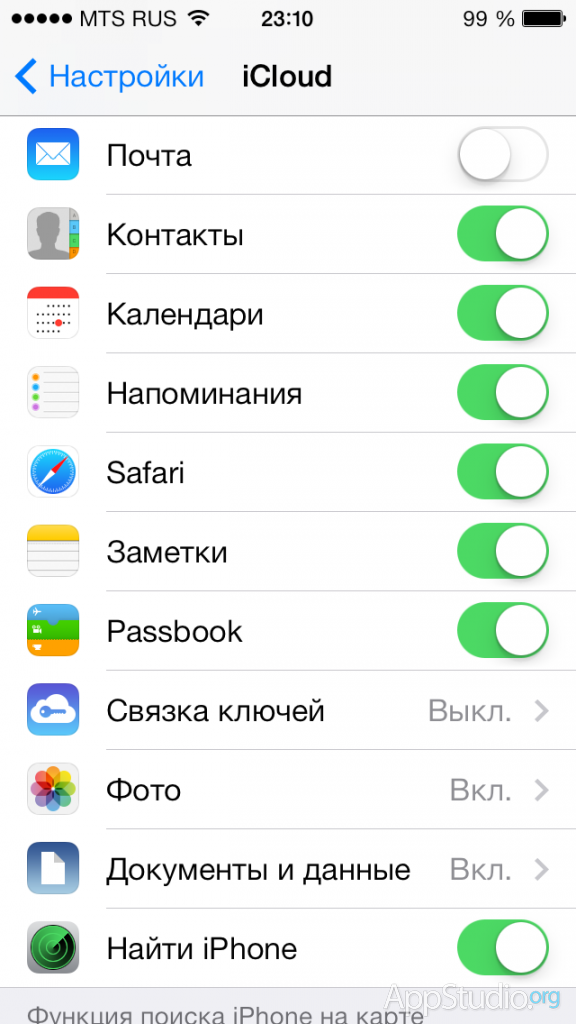
Agree to enable the feature:
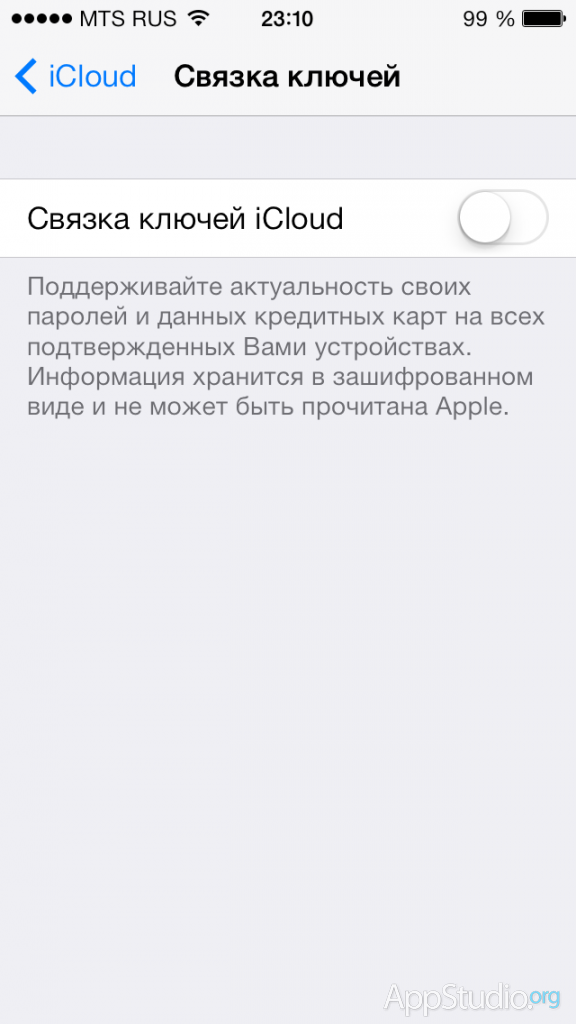
You will definitely need to enter your iCloud password:
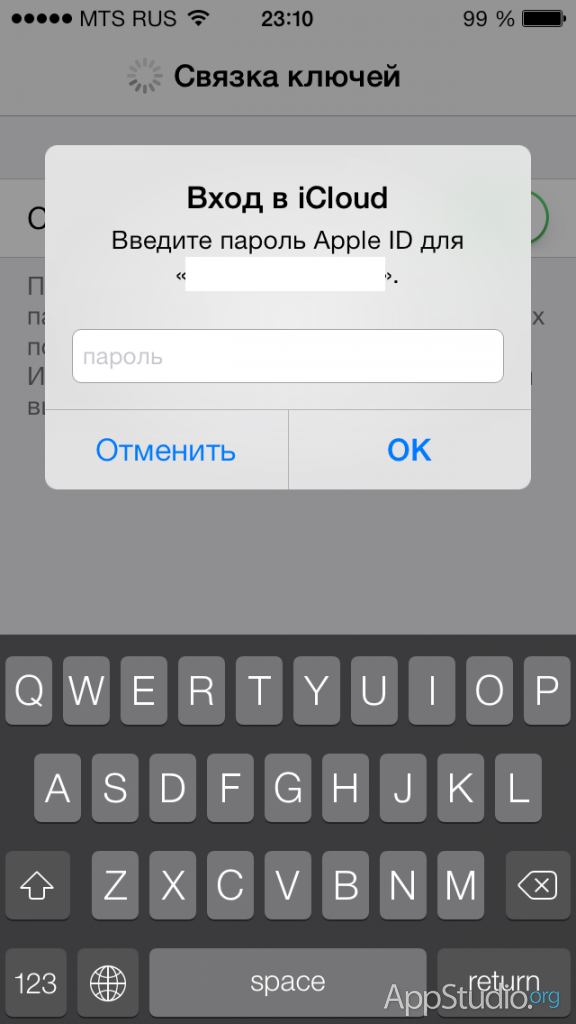
After that, the Keychain will go into activation standby mode.
As we said, when adding a new device to your iCloud Keychain, you have two alternatives:
- enter PIN
- confirm connection from another device
On your iOS device, you will see a "Confirm with code" button, by clicking on which you can enter your PIN and immediately activate the function:

The fallback is confirmation from another device. As soon as you try to turn on iCloud Keychain on one of your devices, all other gadgets connected to the same iCloud account and the same Keychain will receive notifications:
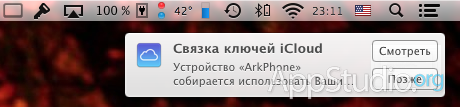
But this is not just a notification. By clicking on the banner, you will be taken to the iCloud settings, where you will be prompted to enter your account password as confirmation of consent to add a new device to your Keychain. After entering the password on any of your other devices, the new gadget is considered to be permanently connected, and password synchronization via iCloud Keychain will begin.
Connect your new Mac to iCloud Keychain
The process is identical to that described in the previous chapter of the review. You go to OS X Settings, iCloud Remote and turn on Keychain Access. Enter your iCloud password.
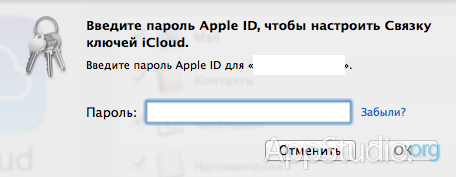
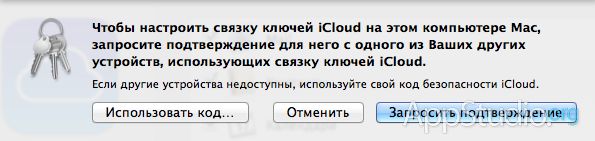
Entering the PIN does not need any special explanations:
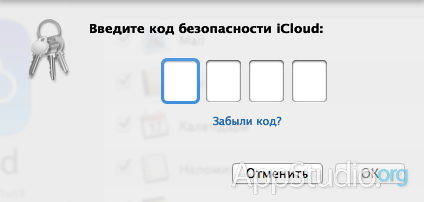
If you do not want to enter your PIN, the Mac will remain in activation standby mode:

It is quite difficult to miss the notification about the need to confirm a new device - in both OS X and iOS it will hang in plain sight:

To have access to Apple services, each user must register an account, which is commonly called an Apple ID. Like any other account, this one also consists of a username and password. As a login, an email address is used, which users "shine" always and everywhere, so it's easy to find out. Given the large set of programs for collecting and cracking passwords, you can get access to your Apple ID today. Apple understands this, so they offer users the protection that is relevant today - two-step authentication. True, this requires a special code, and many users simply do not know where to enter the Apple ID verification code.
By the way, Apple offers 2-Step Verification for iOS 8 (and earlier) users, and for those more fortunate (iOS 9 and older), 2-Step Verification. You still need to know where to enter the Apple ID verification code, because both methods are similar to each other.
What is two-step verification?
it additional protection, thanks to which no one will gain access to the Apple ID, even if he knows the login / password pair. To access, you will still need a specific set of numbers, which he will not have.
If you don't know where to enter your Apple ID verification code, see the following instructions.
- Go to the official website appleid.apple.com. We enter the username and password, a secret code.
- We study the information about the check, which is issued automatically. Then click "Continue". It may be that two-step verification information will not be displayed. You can find it in the section "Change - Security - Configure - Two-step verification".
- In the next window, you must enter the phone number. It will receive SMS codes to complete the check. You don't have to choose your phone number. You can specify the number of parents, wife, etc.
- On the next page, you need to check your phone number. You should receive a code in SMS. Enter it in the window that appears. If it is not there, then click on the "Send code again" button.
- After entering the code, the program will offer to select auxiliary gadgets to receive a verification code. Here you can specify additional trusted smartphones. Each trusted smartphone will have to be confirmed by SMS.
- After confirmation, you will see the recovery key. It is complex and immutable. It must be kept in a safe place - it will be used in the event that you suddenly forget the password to your Apple ID account or simply lose your trusted smartphone.
- In the next window, you will have to enter the recovery code again. This may seem strange to some, but this is normal. This step focuses the user's attention on the importance of the key. Specify the code from the sheet without copying it programmatically.
- The last - we accept the conditions of verification.

That's it. Checking is activated. Now, when you try to sign in to your Apple ID account, you will need an Apple ID verification code. Where to enter it, you now know. The attacker also knows, but he will not be able to enter the account, because he simply will not have a trusted smartphone.
By the way, it is best to indicate the trusted phone not your own, but a close relative. If suddenly someone steals your iPhone, then he can easily log into the Apple ID, because the verification code will be on the same phone.
2-step authentication

There is no practical difference between validation and authentication. At least the user will not notice them. In both cases, you need to know where to enter the Apple ID verification code. In both cases, an SMS comes to the phone with a verification code, after specifying which, access to the account is opened.
Authentication is enabled in the settings. There is a menu item "Password and ...". Also, authentication can be available in the iCloud settings, in the Apple ID tab - "Password and Security". Click on "Enable". Protection will be enabled, but not yet activated.
Now we need to set up authentication. We enter the trusted number, wait for the code, confirm the smartphone. Now the protection is activated, then you need to figure out where to enter the Apple ID verification code. When entering any Apple service, you will need to specify a username and password. And then the code will be sent via SMS. It must be entered after the username / password pair.
What is the difference?
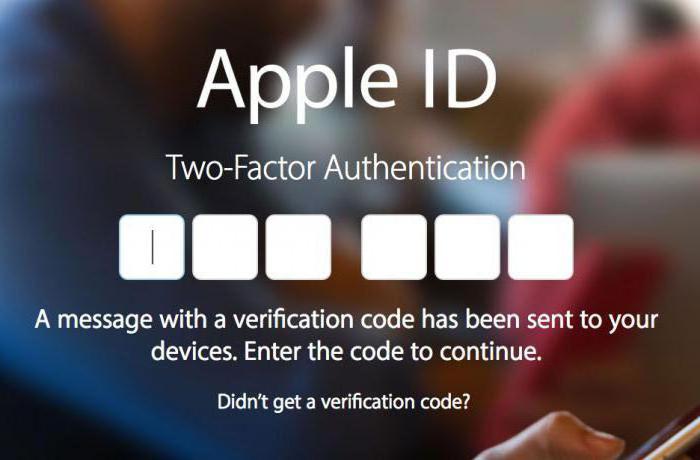
It is easy to see that there is practically no difference between 2-step verification and authentication. In both cases, you need an Apple ID verification code to sign in, so what's the difference?
Apple argues that 2-Step Verification is more secure and modern security. Although the user does not see the difference, the authentication system more efficiently verifies devices and sends confirmation codes. Overall, the optimization is much better.
Now you know where to enter your Apple ID verification code. But first, the protection must be turned on.
Output
I highly recommend using this protection. Regardless of which one you have operating system(old or new), use 2-Step Verification or 2-Step Verification, as this protection negates any efforts by thieves to gain access to your account. Well, if you do not know where to enter the Apple ID verification code, then there will be no problems with this, because user interface so simple that even a child can figure it out.
Two-factor authentication is an additional layer of Apple ID security that ensures that only you can access your account, even if the password is known to someone else.
How it works
With two-factor authentication, your account can only be accessed from trusted iPhone, iPad, or Mac devices. The first time you sign in on a new device, you will need to provide two types of information: your password and a six-digit digital verification code that is automatically displayed on trusted devices. After entering the code, the new device is included in the number of trusted devices. For example, if you have an iPhone, the first time you sign in to your newly purchased Mac, you'll be prompted for a password and verification code, which will automatically appear on your iPhone's screen.
Since knowing the password is not enough to access your account with two-factor authentication, the security of your Apple ID and those stored on servers Apple data increases significantly.
Once you have signed in, a verification code will no longer be prompted on this device until you are completely signed out, all data on the device has been erased, or you need to change your password for security reasons. When you sign in over the Internet, you can specify that the browser is trusted and the next time you sign in from that computer, you will not be prompted for a confirmation code.
Verified devices
A verified device can be an iPhone, iPad, or iPod touch with iOS 9 or later, or a Mac with OS X El Capitan or later that has been signed in using two-factor authentication. This is a device that we know you belong to and that can be used to verify your identity by displaying an Apple verification code when you sign in from another device or browser.
Verified phone numbers
A verified phone number is a number that can be used to receive verification codes via text messages or automatic phone calls. You must verify at least one trusted phone number to have access to two-factor authentication.
You should also consider verifying other trusted numbers that you can access, such as your home phone number or a number used by a family member or close friend. You can use these numbers if you temporarily do not have access to your own devices.
The verification code is different from the one you enter to unlock your iPhone, iPad, and iPod touch.
Set up two-factor authentication for your Apple ID
Two-factor authentication is currently available to iCloud users with at least one device running iOS 9 or OS X El Capitan or later. ...
To turn on two-factor authentication, you can do the following on your iPhone, iPad, or iPod touch.


Enabling two-factor authentication in the "Settings" section
If your device is running iOS 10.3 or later, follow these steps.
- Go to Settings> [your name]> Password & Security.
- Click Continue.
If your device is running iOS 10.2 or earlier, follow these steps.
- Go to Settings> iCloud.
- Select your Apple ID> Password & Security.
- Click Turn On Two-Factor Authentication.
- Click Continue.
You may need to answer your Apple ID security questions.


Entering and confirming a trusted phone number
Specify the phone number to which you need to receive verification codes when entering the system. You can choose to receive the codes as text messages or automatic phone calls.
Enter the verification code to verify your phone number and enable two-factor authentication.
On a Mac with OS X El Capitan or later, follow these steps:
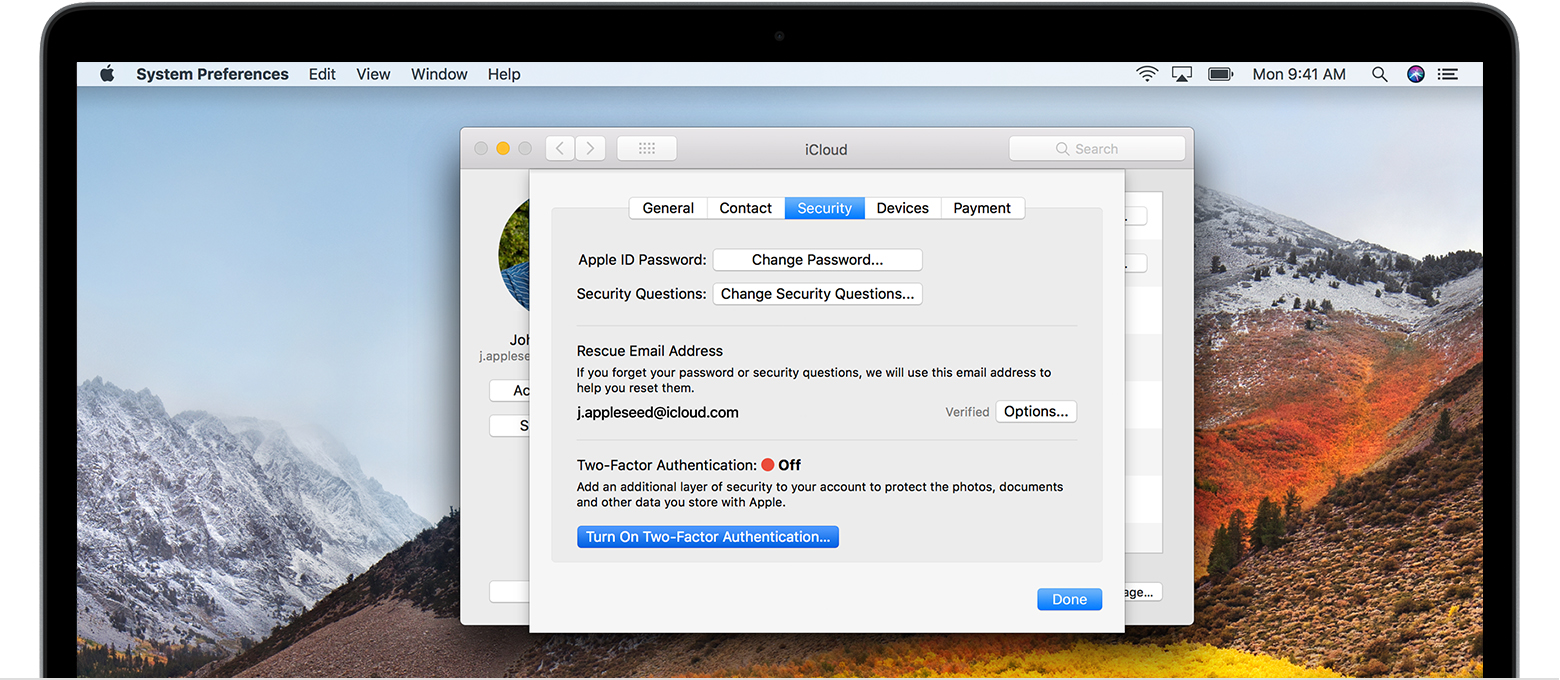
- Choose Apple menu> System Preferences> iCloud> Account.
- Click the Security icon.
- Click Turn On Two-Factor Authentication.
Some Apple IDs created with iOS 10.3 or macOS 10.12.4 and later are protected by two-factor authentication by default. In this case, two-factor authentication will already be enabled.
If you are using two-step verification and want to improve your security,.
If you can't enable two-factor authentication for your account, you can still protect your information.
Things to Remember When Using Two-Factor Authentication
Two-factor authentication greatly enhances Apple ID security. After enabling this feature, you will need a password and access to Trusted Devices or Trusted Phone Number to sign in to your account. To ensure that your account is as secure as possible and that you always have access, there are a few simple guidelines to follow:
- Remember your Apple password ID.
- Use passcodes for all of your devices.
- Update verified phone numbers in a timely manner.
- Ensure the physical safety of trusted devices.
Account management
You can manage your Verified Phone Numbers, Verified Devices, and other account information on.
Timely update of verified phone numbers
To use two-factor authentication, you will need at least one verified phone number in the database to which you can receive verification codes. To update verified phone numbers, follow these steps.
- Go to the Security section and click Edit.
If you need to add a phone number, click Add Verified Phone Number and enter the phone number. Choose how you want to verify your number (text message or automatic phone call) and click Continue. To remove a verified phone number, click next to the phone number you want to remove.
View and manage trusted devices
You can view and manage a list of trusted devices in the Devices section of your Apple ID account page.
- Go to your Apple ID account page.
- Sign in with your Apple ID.
- Go to the "Devices" section.
Creating passwords for programs
When using two-factor authentication to sign in to your account from third-party programs and services, such as non-Apple email, contacts, or calendaring software, will be required. To create a password for the program, follow these steps.
- Sign in to your Apple ID account page.
- Click the Generate Password button under Application Passwords.
- Follow the instructions on the screen.
After creating a password for the program, enter or paste it in the password input field in the program in the usual way.
Help & Frequently Asked Questions
Need help? Perhaps you will find the answers to your questions below.
Is this different from Apple's current two-step verification?
Yes. Two-factor authentication is built directly into iOS, macOS, tvOS, watchOS and websites Apple... It uses other methods of verifying verified devices and providing verification codes, and streamlines overall performance. Two-factor authentication is required for certain features that require increased security.
What should I do if I do not have access to a verified device or the verification code has not been received?
When you sign in and you don't have a trusted device at hand that displays a verification code, the code is sent to the verified phone number via text message or automatic phone call... Click “Code not received” on the login screen and choose to send the code to a verified phone number. Also, the code can be obtained directly from the tested device in the "Settings" menu. ...
How do I regain access to my account if I can't sign in?
If you can't sign in, reset your password, or get confirmation codes, you can. Account recovery is an automated process that will help you gain access to your account as quickly as possible and prevent possible access by other users claiming to be on your behalf. This can take several days - or more - depending on how accurate your account information can be to verify your identity.
Do I need to memorize the answers to security questions now?
No. With two-factor authentication, you don't need to select security questions and remember the answers to them. Your identity is established solely using a password and verification codes sent to your devices and trusted phone numbers. When you start using two-factor authentication, we keep your security questions for two weeks in case you need to return the old security settings for your account. After that, the questions will be deleted.
Can Apple Support help me regain access to my account?
Apple Support can answer your questions about the account recovery process, but cannot verify your identity or expedite the process in any way.
What are the system requirements for two-factor authentication?
For optimal performance, all devices that you use with your Apple ID meet these system requirements:
- iPhone, iPad, or iPod touch with iOS 9 or later
- Mac with OS X El Capitan and iTunes 12.3 or later
- Apple Watch with watchOS 2 or later
- Apple TV (4th generation) with tvOS
- Windows computer with installed programs iCloud for Windows 5 and iTunes 12.3.3 or later.
What if I don't recognize the location shown in the login notification?
When you sign in on a new device, you receive a notification on other tested devices that displays a map showing the approximate location of the new device. This is an approximate location based on the IP address of the device currently in use, not the exact location of the device. The location shown may reflect information about the network you are connected to, rather than your physical location.
If you know that you are the same user who is trying to sign in but do not know the location shown, you can click Allow and continue registering.
However, if you receive a notification that your Apple ID is being used to sign in on a new device and you haven't tried to sign in, click Don't Allow to block the sign-in attempt.
What happens if I use two-factor authentication on a device with earlier versions of the software?
If you are using two-factor authentication on devices running earlier versions of the OS, you may need to add a six-digit verification code at the end of your password when you sign in. on a verified device running iOS 9 or OS X El Capitan or later, or get it to your verified phone number. Then enter your password by adding a six-digit confirmation code to it directly in the password field.
Can I turn off two-factor authentication after turning it on?
Two-factor authentication cannot be disabled for some accounts created with iOS 10.3 or macOS Sierra 10.12.4 and later. If you created your Apple ID in earlier versions of iOS or macOS, you can turn off two-factor authentication.
Remember that after you turn off two-factor authentication, your account will only be protected by a password and security questions.
To turn off two-factor authentication, sign in to your Apple ID account page and click Edit in the Security section. Then click Turn Off Two-Factor Authentication. After you create new security questions and confirm your date of birth, two-factor authentication will be disabled. If your Apple ID account page doesn't have an option to turn off two-factor authentication, then you can't turn it off.
If someone turns on two-factor authentication for Apple ID without your permission, it can also be turned off from the post Email with registration confirmation sent to your Apple ID or backup email address. Click Turn Off Two-Factor Authentication at the bottom of your email to restore your previous Apple ID security settings and control your account... The link is active for two weeks after registration.
Date of publication: 19.09.2017