In this article I will tell you how you can insure yourself against the possible loss of your phone. After following the instructions, you will be able to:
- find your android phone or tablet(you can find out the approximate location of the device)
- remotely lock phone/tablet
- through the Internet delete personal data from the device
In order for the service to work you need:
- current
- internet access on phone
- enabled geolocation on the device (GPS)
Internet access is needed to communicate with the phone, GPS to determine and transmit coordinates, Google account - to manage the service " Android remote control »
If all this is there, then you can proceed to setting up the Android Remote Control service. First, let's set up the phone, you need to enable remote control. To do this, go to the menu, item "Settings" - settings "Google" - "Security". We include here the items "Remote device search" and "Remote lock and reset settings":





Let's also check if the geolocation function (GPS) is enabled. To do this, go to the "Menu" - "Settings" - "Location" - move the switch to the "ON position"




And also mobile Internet or WiFi must be enabled on the phone. This completes the setup.
Now let's check if the service is working. We go to a computer or laptop and open the page in the browser https://www.google.com/android/devicemanager?hl=ru. Here we enter the Google account data from our Android and after that the service page will load:
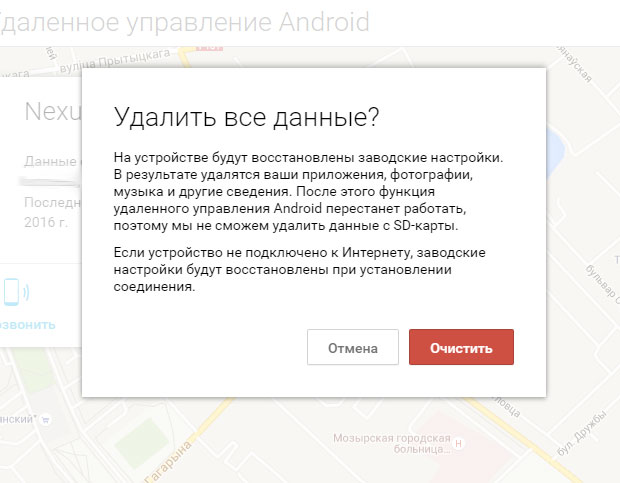
Here we see the location of our device and 3 available functions: ring, block, clear.
If the phone or tablet is not visible in the service, then it may be hidden in Google Play, to display it, you need to enable the "Show in menu" function on the page play.google.com/settings
For the simplest test, click "Ring" if everything is set up correctly, then the phone should ring.

When you select the "Lock" function, you can set a new password for improved locking. And you can also set a message that will be displayed on the lock screen, for example, “Reward for return! My number is +77-777-777.” And you can also set the allowed phone number, this is the only number that you can call and it will be displayed on the lock screen.

And the last function is cleaning the phone. If there is information on the phone that should not fall into the hands of other people and there are doubts that the phone will be found, then you can delete all data on the phone.
That's all, if you have any questions, you can ask them in the comments 🙂
Do you really value your personal data and files that are on your smartphone or tablet? Android provides multi-level protection that allows you to protect the contents of your device.
Suppose you have an Android smartphone or tablet and suddenly it was stolen... Naturally, the loss of your favorite mobile device is already a big loss, but absolutely all your files and data will become available to an attacker if you have quite confidential information or credit card data there, then this is a significant loss! In this article, I will give solutions that how to protect yourself from falling into the wrong hands of personal information.
Connected Google Account
It seemed that what does having a Google account have to do with it? If you connect a Google account, then you can use the device management service and remotely detect Android, block it or delete all your personal data, but the only thing is that you must always have the Internet turned on.

Secure Screen Lock
Undoubtedly remote blocking or deleting all information is a great way to keep information safe, but if the device is blocked in a simple conventional way

the attacker will have time to quickly turn off the Internet and then you will not be able to delete anything. It is worth thinking about a more secure way to block. In Settings -> Lock Screen -> Screen Security -> Screen Lock

it is possible to choose other methods of blocking, more secure:
- Slider - normal blocking
- Face Unlock - Unlock the screen by showing your face (unreliable, your printed photo of your face or video is enough)
- Graphic key - entering a secret pattern (the most reliable)
- PIN code (not SIM) - enter a digital password to unlock (secure)
- Password - enter an alphanumeric password (strong)

PIN code of the SIM card
Since we have already talked about security, it is worthwhile to additionally enable the PIN code on the SIM card, this will allow you to block the device even at the stage of turning it on. Also, the PIN code on the SIM will allow you to be sure that no one can use it and save the data on the card. To enable the PIN code on the SIM, go to the menu Settings -> Security -> Set up blocking -> Sim card blocking

Hide files
Of course, this method will not protect 100% from an attacker, but at least it will allow for a certain period of time to keep them invisible. For more information on how to hide files, read the dedicated article on hiding data.
Data encryption
This method will allow you to be 100% sure that your data will not fall into the wrong hands, and here's why: if the attacker failed to crack the PIN code of the SIM card and he threw it away, or if he stole the memory card, then all these files will be encrypted and not can use them. Therefore, the Data Encryption method, coupled with the previous methods, gives the best effect. In order to enable encryption, go to Settings - Security - Encrypt data, then put the device on charge and start the process. Please note that the process cannot be interrupted and it lasts at least one hour!

How to make life a little easier - Smart Lock
Of course, the security of personal information is good, but sometimes entering passwords infuriates you! Since Android 5.0 Lollipop, Google has introduced a new Smart Lock feature. The meaning of this Smart Lock feature is to make life easier without having to enter a password or key once again. Read more in a special article about Smart Lock.
App lock
Let's say you need to give a friend your Android smartphone or tablet, but you don't want him to go to other applications and see personal information. Since Android 5.0 Lollipop, Google has added a new feature " app blocking" which allows you to pin one single application on the screen without the ability to exit it in the standard way.
How to enable "app lock"?
Go to Settings -> Security -> App lock

Now, to activate this feature, click the "overview of all running applications" button (square) and click the pin button on the required application. To exit this function, press the "overview of all running applications" and "back" buttons.

You can see how this function works in general in the video attached below.
(rutube)feb3798ad4ab5ccb1c967178049d2b52(/rutube)
Due to reports of malicious attacks and data leaks, many users are looking to protect their mobile phones from hackers. To do this, you need to ensure the security of the smartphone, increase the strength of the password and protect the data. Nothing will make your device 100% secure, but some steps on your part will reduce the chances of your phone being hacked.
Steps
How to secure your phone
- Secure wireless networks are marked with a lock icon.
-
Turn off your wireless network, Bluetooth, and mobile data when not in use. A hacker won't hack into a phone if it's not connected to the internet. Follow the instructions in the user manual or in the support section of the phone manufacturer's website.
- Turn on Airplane Mode is a quick way to disable all networks on your phone.
-
Charge your phone with reliable USB ports. These include ports on your computer and in your vehicle. Hackers can break into public USB ports, such as cafes or airports, and steal personal information.
- If you are traveling, please bring your AC adapter and USB cable with you. Hackers will not be able to hack into your phone through a USB adapter.
-
Opt out of automatic authorization. It is convenient, but allows you to quickly hack the device. Therefore, we recommend that you enter your username and password every time, especially on pages with banking and other confidential information. Enter characters slowly to avoid blocking.
Use different passwords. If you set the same password for your mailbox, bank account, and social networking apps, a hacker can easily crack them. Take the time to come up with reliable combinations of letters, numbers, and symbols for each account. If there is no time, the password manager is able to quickly generate many strong passwords.
Change passwords regularly. Create a schedule and follow it, i.e. change passwords weekly, monthly or quarterly. If you want, create a reminder about this in your calendar.
Update your operating system. Whenever your iOS or Android smartphone notifies you that a system update is available, download and install it. Many hackers exploit vulnerabilities in outdated operating systems. Updates fix vulnerabilities and make the phone more secure.
Install the security app on your Android smartphone. Do not download any application. Read the recommendations in reliable sources, for example, on habr.com. Also choose an antivirus from a well-known company, such as Kaspersky, Norton, McAfee, Avast or Bitdefender. Antivirus applications from well-known companies are better at detecting viruses than applications from unknown companies.
Set a password. It should be complex but easy to remember. Don't include birth dates, pet names, banking PINs, or phone numbers in your password. Follow the instructions from Apple or Android Support to set up a password.
Install trusted apps. Download them only from reliable sources (App Store or Play Store) and only from well-known developers. Be careful if you're using an Android smartphone - Google doesn't check its apps as thoroughly as Apple does. Before you install the application, read the reviews about it.
Learn how to control your phone remotely. Settings or apps allow you to remotely lock and delete data from your phone if it is stolen. If you have a new smartphone model, third-party applications are not needed - you can manage your iPhone using Find My iPhone in iCloud. You can secure your Android smartphone through your Google account using Android Device Manager.
Be careful when using unsecured wireless networks. Such networks are not marked with a padlock icon. Try not to use them - it is better to turn on the mobile Internet. Otherwise, install a VPN app that will reroute your traffic over encrypted connections. Even if you use a VPN on an unsecured wireless network, never open your bank account page and don't share sensitive information.
How to protect data
Do not share personal information on social networks. Enter your real name, but never give your address, phone number, mother's maiden name, or similar information on your profile. Moreover, we do not recommend disclosing less important information, such as your favorite song or the book you are currently reading. Hackers can use this information to steal your identity.
The mobile phone is one of the most popular objects of theft. This device is easy to take away, and any reseller will immediately purchase it at half price. But technologies are gradually emerging that make such actions meaningless. And today we will talk about 5 innovative ways to protect your smartphone.
Remote phone lock
This practice has already been successfully tested by Apple in their laptops. Its essence lies in the ability to remotely block all the functions of the device if it is lost or stolen.
Now phone owners can download such a program in app stores, but this lock can be easily bypassed by resetting the smartphone or flashing it. But the originally built-in kill switch function assumes the complete destruction of the device's filling, all personal data and files by a unique IMEI number. And this will prevent the information important to the owner from falling into the hands of strangers, and in general will make it impossible to work with a stolen device.

The South Korean government, concerned about the increase in the number of thefts of mobile phones by one and a half times in a year, is going to oblige manufacturers to equip all phones with a kill switch function. Samsung was the first to decide on this innovation - its new Samsung Galaxy S5 is equipped with the ability to search for a smartphone and remotely lock it.
Fingerprints
For a century, fingerprints have been used primarily in forensic science. But in a few years, portable scanners may appear in the pockets of most people in the world. After all, mobile phone manufacturers have begun to use unique skin patterns on fingers for each person to identify a smartphone user.
When the phone is turned on, the owner only needs to put his finger on the scanner to unlock his smartphone in this way. At the same time, relatives or friends of the user can use the same right if their fingerprints are also included in the database of the device. But strangers will not be able to turn on the smartphone under any circumstances.

Now manufacturers equip their top models of mobile phones with a fingerprint scanner, for example, such a function is available in the iPhone 5S, HTC One Max, Samsung Galaxy S5, Motorola ES400 and some other devices.
Phone alarm
Another popular way to protect your phone from theft is to install an audible alarm on it. Unlike the functions mentioned above, this one is available not only for top models, but for any smartphone. After all, the program can be downloaded from the application store, and it will work even on the cheapest device.
Different developers offer different options. Some applications start a sound signal when you disconnect your smartphone from the charger. There are programs that are activated every time you touch an unattended phone. And there are such developments that allow you to turn on the alarm remotely - via SMS with a special set of characters or via the Internet.
Phone self-destruct
This technology has been developed but has not yet been implemented in the production of mobile phones. It is based on a special polymer board, which can melt at a signal from the outside, after which the device cannot be used.The first mobile phone equipped with such a card was presented in early April at an exhibition in Dallas by scientists from the University of Iowa. In front of many viewers, the insides of the device were melted after sending an SMS to it.

According to the creators of this technology, it can be used in the production of mobile phones and bank cards - two items, the loss or theft of which can lead to significant trouble for the former owner.
Password in the charger
Two years ago, Apple patented perhaps the most radical system for protecting laptops and mobile phones from theft. The developers suggest storing an additional password to the device in a special memory module built into the charger.After all, the password in the phone can be bypassed by changing the firmware. But such fraud will become meaningless if the smartphone loses its original charger, which is one of the parts of mobile phone authentication.

An attacker will not be able to start a mobile phone after the battery is discharged in it, the device will refuse to accept someone else's charging. At the same time, the owner of the phone himself can easily use someone else's charger, knowing the additional password recognized by the smartphone.