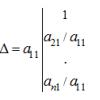Cryptographic tools - these are special mathematical and algorithmic means of protecting information transmitted through communication systems and networks, stored and processed on a computer using a variety of encryption methods.
Technical information protection by transforming it, excluding its reading by unauthorized persons, has worried a person for a long time. Cryptography must provide such a level of secrecy that it is possible to reliably protect critical information from decryption by large organizations such as the mafia, multinational corporations and large states. In the past, cryptography was only used for military purposes. However, now, with the emergence of the information society, it becomes a tool for ensuring confidentiality, trust, authorization, electronic payments, corporate security and countless other important things. Why has the problem of using cryptographic methods become especially urgent at the moment?
On the one hand, the use of computer networks has expanded, in particular the global Internet network, through which large volumes of information of a state, military, commercial and private nature are transmitted, which does not allow unauthorized persons to access it.
On the other hand, the emergence of new powerful computers, technologies of network and neural computing made it possible to discredit cryptographic systems, which were considered practically undetected until recently.
Cryptology (kryptos - secret, logos - science) deals with the problem of protecting information by transforming it. Cryptology is divided into two areas - cryptography and cryptanalysis. The goals of these directions are exactly the opposite.
Cryptography is concerned with finding and researching mathematical methods for transforming information.
The sphere of interest of cryptanalysis is the study of the possibility of decrypting information without knowing the keys.
Modern cryptography includes 4 major sections.
· Symmetric cryptosystems.
· Cryptosystems with a public key.
· Electronic signature systems.
· Key management.
The main directions of using cryptographic methods are the transfer of confidential information through communication channels (for example, e-mail), the authentication of transmitted messages, the storage of information (documents, databases) on media in an encrypted form.
Terminology.
Cryptography makes it possible to transform information in such a way that its reading (recovery) is possible only with knowledge of the key.
As information to be encrypted and decrypted, texts based on a certain alphabet will be considered. These terms mean the following.
Alphabet- a finite set of characters used to encode information.
Text- an ordered set of elements of the alphabet.
Encryption- transformation process: the original text, which is also called plain text, is replaced by cipher text.
Decryption- the reverse process to encryption. Based on the key, the ciphertext is converted to the original one.
Key- information necessary for unhindered encryption and decryption of texts.
The cryptographic system is a family of T [T1, T2, ..., Tk] transformations of the plain text. Members of this family are indexed, or denoted by the symbol "k"; the parameter to is the key. The key space K is the set of possible key values. Typically, a key is a sequential series of letters of the alphabet.
Cryptosystems are divided into symmetric and public key.
In symmetric cryptosystems, the same key is used for both encryption and decryption.
Public key systems use two keys, public and private, which are mathematically related to each other. Information is encrypted using a public key that is available to everyone, and decrypted using a private key known only to the recipient of the message.
The terms key distribution and key management refer to the processes of an information processing system, the content of which is the compilation and distribution of keys among users.
An electronic (digital) signature is a cryptographic transformation attached to the text, which allows, when the text is received by another user, to verify the authorship and authenticity of the message.
Crypto resistance is called the characteristic of the cipher, which determines its resistance to decryption without knowing the key (i.e., cryptanalysis).
The effectiveness of encryption in order to protect information depends on maintaining the secret of the key and the cryptographic strength of the cipher.
The simplest criterion for such efficiency is the probability of key disclosure or the cardinality of the set of keys (M). Essentially, this is the same as cryptographic strength. To estimate it numerically, you can also use the complexity of decrypting the cipher by enumerating all the keys.
However, this criterion does not take into account other important requirements for cryptosystems:
· Impossibility of disclosure or meaningful modification of information based on an analysis of its structure;
· The perfection of the used security protocols;
· The minimum amount of used key information;
· Minimal complexity of implementation (in the number of machine operations), its cost;
· High efficiency.
Expert judgment and simulation are often more effective in selecting and evaluating a cryptographic system.
In any case, the selected complex of cryptographic methods should combine both convenience, flexibility and efficiency of use, as well as reliable protection from intruders of information circulating in the IS.
This division of information security means ( technical protection of information), is rather arbitrary, since in practice they very often interact and are implemented in a complex in the form of software and hardware modules with extensive use of information closure algorithms.
Conclusion
In this course work, I examined the local computer network of the Administration, and concluded that for complete protection of information, it is necessary to apply all means of protection in order to minimize the loss of this or that information.
As a result of the work done: computerization of workplaces with their integration into a local computer network, with the presence of a server and access to the Internet. The implementation of this work will ensure the fastest and most productive work of the working personnel.
The tasks that were set when receiving the task, in my opinion, have been achieved. A diagram of the local area network of the Administration is given in Appendix B.
Bibliography.
1. GOST R 54101-2010 “Automation and control systems. Security means and systems. Maintenance and running repairs "
2. Organizational protection of information: a textbook for universities Averchenkov VI, Rytov M.Yu. 2011
3. Khalyapin D.B., Yarochkin V.I. Fundamentals of information security.-M.: IPKIR, 1994
4. Khoroshko V.A., Chekatkov A.A. Methods and means of information protection (edited by Kovtanyuk) K .: Junior Publishing House, 2003.-504s.
5. Hardware and computer networks Ilyukhin B.V. 2005
6. Yarochkin V.I. Information Security: A Textbook for University Students.-M.: Academic Project!?! Foundation "Mir", 2003.-640s.
7.http: //habrahabr.ru
8.http: //www.intel.com/ru/update/contents/st08031.htm
9.http: //securitypolicy.ru
10.http: //network.xsp.ru/5_6.php
Note A.
Note B.

The means of cryptographic protection of information (CIP) include hardware, software and hardware and software that implement cryptographic algorithms for transforming information in order to:
Protection of information during its processing, storage and transmission through the transport environment of the nuclear power plant;
Ensuring the reliability and integrity of information (including the use of digital signature algorithms) during its processing, storage and transmission over the transport environment of the nuclear power plant;
Generation of information used to identify and authenticate subjects, users and devices;
Generation of information used to protect the authenticating elements of the protected AS during their generation, storage, processing and transmission.
It is assumed that cryptographic information protection tools are used in some AS (in a number of sources - information and telecommunication system or communication network), together with mechanisms for the implementation and guarantee of security policy.
Cryptographic transformation has a number of essential features:
In the CIPF, a certain information transformation algorithm is implemented (encryption, electronic digital signature, integrity control)
Input and output arguments of the cryptographic transformation are present in the AS in some material form (AS objects)
CIPF uses some confidential information (keys) for work
The cryptographic transformation algorithm is implemented in the form of some material object interacting with the environment (including the subjects and objects of the protected AS).
Thus, the role of CIPF in a protected AS is the transformation of objects. In each specific case, the specified transformation has specific features. So, the encryption procedure uses the object - plain text and the object - key as input parameters, the result of the transformation is the object - the encrypted text; on the contrary, the decryption procedure uses the ciphertext and the key as input parameters; the procedure for applying a digital signature uses as input parameters an object - a message and an object - a secret signature key, the result of a digital signature is an object - a signature, as a rule, integrated into an object - a message. We can say that the CIPF protects objects at the semantic level. At the same time, objects - parameters of a cryptographic transformation are full-fledged AS objects and can be objects of some security policy (for example, encryption keys can and should be protected from tampering systems, public keys for verifying digital signatures from changes). So, cryptographic information protection devices as part of protected AS have a specific implementation - it can be a separate specialized device built into a computer, or a specialized program. The following points are essential:
CIPF exchanges information with the external environment, namely: keys are entered into it, plain text during encryption
In the case of hardware implementation, the CIPF uses an element base of limited reliability (i.e., in the details that make up the CIPF, malfunctions or failures are possible)
CIPF in the case of software implementation is performed on a processor of limited reliability and in a software environment containing extraneous programs that can affect various stages of its operation
CIPF is stored on a tangible medium (in the case of software implementation) and may be intentionally or accidentally distorted during storage
CIPF interacts with the external environment in an indirect way (it is powered from the mains, emits electromagnetic fields)
CIPF is manufactured and / or used by a person who can make mistakes (intentional or accidental) in the development and operation
The existing means of data protection in telecommunication networks can be divided into two groups according to the principle of building a key system and an authentication system. The first group includes the means that use symmetric cryptoalgorithms to build the key system and the authentication system, the second - asymmetric ones.
Let's carry out a comparative analysis of these systems. An information message ready for transmission, initially open and unprotected, is encrypted and thereby converted into a cipher, that is, into a closed text or graphic image of a document. In this form, the message is transmitted over a communication channel, even not secure. After receiving the message, the authorized user decrypts it (i.e., reveals) by reverse transforming the cryptogram, as a result of which the original, open form of the message is obtained, available for perception by authorized users. The conversion method in a cryptographic system corresponds to the use of a special algorithm. The action of such an algorithm is triggered by a unique number (sequence of bits), usually called an encryption key.
For most systems, the key generator scheme can be a set of instructions and commands, either a hardware node, or a computer program, or all of these together, but in any case, the encryption (decryption) process is implemented only by this special key. For the exchange of encrypted data to be successful, both the sender and the recipient must know the correct key setting and keep it secret. The strength of any closed communication system is determined by the degree of secrecy of the key used in it. However, this key must be known to other users on the network so that they can freely exchange encrypted messages. In this sense, cryptographic systems also help to solve the problem of authentication (authentication) of the received information. The attacker, in the event of intercepting a message, will deal only with cipher text, and the true recipient, accepting messages closed with a key known to him and the sender, will be reliably protected from possible disinformation. In addition, it is possible to encrypt information in a simpler way - using a pseudo-random number generator. The use of a pseudo-random number generator consists in generating a cipher gamma using a pseudo-random number generator with a certain key and superimposing the resulting gamma on open data in a reversible way. This method of cryptographic protection is quite easy to implement and provides a fairly high encryption speed, but it is not sufficiently resistant to decryption.
Classical cryptography is characterized by the use of one secret unit - a key that allows the sender to encrypt the message and the recipient to decrypt it. In the case of encryption of data stored on magnetic or other storage media, the key allows you to encrypt information when written to the media and decrypt when reading from it.
"Organizational and legal methods of information security"
Basic regulatory guidance documents related to state secrets, regulatory reference documents
To date, our country has created a stable legislative framework in the field of information protection. The fundamental law is the Federal Law of the Russian Federation "On Information, Information Technologies and Information Protection". "State regulation of relations in the field of information protection is carried out by establishing requirements for the protection of information, as well as liability for violation of the legislation of the Russian Federation on information, information technology and information protection." The Law also establishes the obligations of information owners and operators of information systems.
As for the "codified" regulation of information security, the norms of the Code of Administrative Offenses of the Russian Federation and the Criminal Code of the Russian Federation also contain the necessary articles. In Art. 13.12 of the Code of Administrative Offenses of the Russian Federation speaks of a violation of information protection rules. Also Art. 13.13, which provides for punishment for illegal activities in the field of information protection. And Art. 13.14. which provides for penalties for disclosing information with limited access. Article 183. The Criminal Code of the Russian Federation provides for punishment for illegal receipt and disclosure of information constituting commercial, tax or banking secrets.
The Federal Law “On Information, Informatization and Information Protection” stipulates that the state information resources of the Russian Federation are open and publicly available. An exception is documented information classified by law as a restricted access category.
The concept of state secrets is defined in the Law "On state secrets" as "information protected by the state in the field of its military, foreign policy, economic, intelligence, counterintelligence and operational-search activities, the dissemination of which may harm the security of the Russian Federation." Thus, based on the balance of interests of the state, society and citizens, the scope of the Law is limited to certain types of activities: military, foreign policy, economic, intelligence, counterintelligence and operational-search.
The law determined that the main criterion is the belonging of classified information to the state.
The law also enshrined the creation of a number of bodies in the field of protecting state secrets, in particular, an interdepartmental commission for the protection of state secrets, introduced the institution of officials empowered to classify information as state secrets, while imposing personal responsibility on them for activities to protect state secrets in their area of responsibility.
The general organization and coordination of work in the country on the protection of information processed by technical means is carried out by a collegial body - the Federal Service for Technical and Export Control (FSTEC) of Russia under the President of the Russian Federation, which exercises control over the provision in government bodies and at enterprises conducting work on defense and other secret topics.
Purpose and tasks in the field of information security at the state level
The state policy of ensuring the information security of the Russian Federation determines the main directions of the activities of federal bodies of state power and bodies of state power of the constituent entities of the Russian Federation in this area, the procedure for securing their responsibilities to protect the interests of the Russian Federation in the information sphere within the framework of their activities and is based on maintaining a balance of personal interests , society and the state in the information sphere. The state policy of ensuring the information security of the Russian Federation is based on the following basic principles: observance of the Constitution of the Russian Federation, legislation of the Russian Federation, generally recognized principles and norms of international law in the implementation of activities to ensure information security of the Russian Federation; openness in the implementation of the functions of federal bodies of state power, bodies of state power of the constituent entities of the Russian Federation and public associations, which provides for informing the public about their activities, taking into account the restrictions established by the legislation of the Russian Federation; legal equality of all participants in the information interaction process, regardless of their political, social and economic status, based on the constitutional right of citizens to freely search, receive, transfer, produce and disseminate information in any legal way; priority development of domestic modern information and telecommunication technologies, production of hardware and software that can ensure the improvement of national telecommunication networks, their connection to global information networks in order to comply with the vital interests of the Russian Federation.
The state in the process of implementing its functions to ensure the information security of the Russian Federation: conducts an objective and comprehensive analysis and forecasting of threats to the information security of the Russian Federation, develops measures to ensure it; organizes the work of the legislative (representative) and executive bodies of state power of the Russian Federation to implement a set of measures aimed at preventing, repelling and neutralizing threats to the information security of the Russian Federation; supports the activities of public associations aimed at objectively informing the population about socially significant phenomena of public life, protecting society from distorted and inaccurate information; exercises control over the development, creation, development, use, export and import of information security tools through their certification and licensing of information security activities; conducts the necessary protectionist policy in relation to manufacturers of information technology and information protection in the territory of the Russian Federation and takes measures to protect the internal market from the penetration of low-quality information technology and information products; contributes to the provision of individuals and legal entities with access to world information resources, global information networks; formulates and implements the state information policy of Russia; organizes the development of a federal program for ensuring the information security of the Russian Federation, combining the efforts of state and non-state organizations in this area; contributes to the internationalization of global information networks and systems, as well as the entry of Russia into the world information community on the basis of equal partnership.
Improving the legal mechanisms for regulating public relations arising in the information sphere is a priority direction of state policy in the field of ensuring information security of the Russian Federation.
This implies: an assessment of the effectiveness of the application of existing legislative and other normative legal acts in the information sphere and the development of a program for their improvement; creation of organizational and legal mechanisms for ensuring information security; determination of the legal status of all subjects of relations in the information sphere, including users of information and telecommunication systems, and establishment of their responsibility for compliance with the legislation of the Russian Federation in this area; creation of a system for collecting and analyzing data on the sources of threats to the information security of the Russian Federation, as well as on the consequences of their implementation; the development of normative legal acts that determine the organization of the investigation and the procedure for judicial proceedings on the facts of illegal actions in the information sphere, as well as the procedure for eliminating the consequences of these illegal actions; development of offenses, taking into account the specifics of criminal, civil, administrative, disciplinary liability and the inclusion of relevant legal norms in the criminal, civil, administrative and labor codes, in the legislation of the Russian Federation on public service; improving the system of training personnel used in the field of ensuring information security of the Russian Federation.
Legal support of the information security of the Russian Federation should be based, first of all, on the observance of the principles of legality, the balance of interests of citizens, society and the state in the information sphere. Compliance with the principle of legality requires federal bodies of state power and bodies of state power of the constituent entities of the Russian Federation, when resolving conflicts arising in the information sphere, to strictly be guided by legislative and other normative legal acts regulating relations in this area. Compliance with the principle of balancing the interests of citizens, society and the state in the information sphere presupposes the legislative consolidation of the priority of these interests in various areas of the life of society, as well as the use of forms of public control over the activities of federal bodies of state power and bodies of state power of the constituent entities of the Russian Federation. Implementation of guarantees of constitutional human and civil rights and freedoms related to activities in the information sphere is the most important task of the state in the field of information security. The development of mechanisms for the legal support of the information security of the Russian Federation includes measures for the informatization of the legal sphere as a whole. In order to identify and coordinate the interests of federal government bodies, government bodies of the constituent entities of the Russian Federation and other subjects of relations in the information sphere, to develop the necessary decisions, the state supports the formation of public councils, committees and commissions with a wide representation of public associations and promotes the organization of their effective work.
Features of certification and standardization of cryptographic services
In almost all countries with developed cryptographic technologies, the development of cryptographic information protection tools belongs to the sphere of state regulation. State regulation, as a rule, includes licensing of activities related to the development and operation of cryptographic means, certification of cryptographic information protection tools and standardization of algorithms for cryptographic transformations.
The following activities are subject to licensing: development, production, certification tests, implementation, operation of encryption tools intended for cryptographic protection of information containing information constituting state or other secrets protected by law, during its processing, storage and transmission through communication channels, as well as provision of services in the field of encryption of this information; development, production, certification tests, operation of telecommunication systems and complexes of the highest bodies of state power of the Russian Federation; development, production, certification tests, implementation, operation of closed systems and telecommunication complexes of authorities of the constituent entities of the Russian Federation, central federal executive authorities, organizations, enterprises, banks and other institutions located on the territory of the Russian Federation, regardless of their departmental affiliation and forms property (hereinafter referred to as closed systems and telecommunication complexes) intended for the transmission of information constituting a state or other secret protected by law; carrying out certification tests, implementation and operation of encryption tools, closed systems and telecommunication complexes designed to process information that does not contain information constituting state or other secrets protected by law, during its processing, storage and transmission through communication channels, as well as the provision of services in the field encrypting this information
Encryption means include: hardware, software and hardware-software that implement cryptographic algorithms for converting information, ensuring the security of information during its processing, storage and transmission through communication channels, including encryption technology; hardware, software and hardware-software means of protection against unauthorized access to information during its processing and storage that implement cryptographic algorithms for converting information; hardware, software and hardware-software means of protection against the imposition of false information that implement cryptographic algorithms for converting information, including means of imitation protection and "digital signature"; hardware, hardware-software and software tools for the production of key documents for encryption tools, regardless of the type of key information carrier.
Closed systems and complexes of telecommunications include systems and complexes of telecommunications, which ensure the protection of information using encryption tools, protected equipment and organizational measures.
Additionally, the following activities are subject to licensing: operation of encryption tools and / or digital signatures, as well as encryption tools for protecting electronic payments using plastic credit cards and smart cards; provision of services for the protection (encryption) of information; assembly, installation, adjustment of encryption tools and / or digital signatures, encryption tools to protect electronic payments using plastic credit cards and smart cards; development of encryption tools and / or digital signatures, encryption tools to protect electronic payments using plastic credit cards and smart cards
The procedure for certification of cryptographic information protection tools is established by the "System of certification of means of cryptographic protection of information ROSS.R11.0001.030001 of the State Standard of Russia.
Standardization of algorithms for cryptographic transformations includes comprehensive research and publication in the form of standards of elements of cryptographic procedures in order to use approved cryptographically strong transformations by developers of cryptographic information protection tools, ensure the possibility of joint operation of various cryptographic information protection tools, as well as the possibility of testing and checking the compliance of the cryptographic information protection tool with a specified standard algorithm. The following standards have been adopted in Russia - the algorithm for cryptographic transformation 28147-89, algorithms for hashing, setting and verifying digital signatures P34.10.94 and P34.11.94. Among foreign standards, DES, RC2, RC4 encryption algorithms, MD2, MD4 and MD5 hashing algorithms, DSS and RSA digital signature setting and verification algorithms are widely known and applied.
Legislative base of information security
Basic concepts, requirements, methods and tools for designing and assessing an information security system for information systems (IS) are reflected in the following fundamental documents:
"Orange Book" of the National Center for Computer Protection
"Harmonized European Countries Criteria (ITSEC)";
The concept of protection against unauthorized attacks of the State Commission under the President of the Russian Federation.
Information security concept
The security concept of the system being developed is "a set of laws, rules and norms of behavior that determine how an organization processes, protects and disseminates information. In particular, the rules determine in which cases the user has the right to operate with certain sets of data. The more reliable the system, the stricter and the security concept should be more diverse. Depending on the formulated concept, you can choose specific mechanisms that ensure the security of the system. The security concept is an active component of protection, including the analysis of possible threats and the choice of countermeasures. "
The security concept of the system being developed according to the Orange Book should include the following elements:
Arbitrary access control;
Object reuse safety;
Security labels;
Compulsory access control.
Consider the content of the listed elements.
Arbitrary access control is a method of restricting access to objects based on the identity of the subject or the group to which the subject belongs. Arbitrariness of control lies in the fact that some person (usually the owner of the object) can, at his discretion, give other subjects or take away their access rights to the object.
The main advantage of arbitrary access control is flexibility, the main disadvantages are the dispersion of control and the complexity of centralized control, as well as the isolation of access rights from data, which allows copying secret information into public files.
Object reuse security is an important practical addition to access controls to prevent accidental or deliberate extraction of sensitive information from garbage. Reuse security must be guaranteed for areas of RAM (in particular, for buffers with screen images, decrypted passwords, etc.), for disk blocks and magnetic media in general.
Security labels are associated with subjects and objects to enforce access control. The subject's label describes his trustworthiness, the object's label - the degree of secrecy of the information contained in it. According to the Orange Book, security labels have two parts - the level of secrecy and the list of categories. The main problem that needs to be addressed with regard to tags is ensuring their integrity. First, there should be no untagged subjects or objects, or there will be easily exploitable holes in tagged security. Secondly, for any operations with data, the labels must remain correct. One of the means of ensuring the integrity of security labels is the division of devices into multi-level and single-level devices. Information of different levels of secrecy (more precisely, lying in a certain range of levels) can be stored on multilevel devices. A single-level device can be viewed as a degenerate case of a multi-level device, when the valid range consists of one level. Knowing the level of the device, the system can decide whether it is permissible to write information to it with a specific label.
Access control enforcement is based on matching the security labels of the subject and the object. This method of access control is called enforced because it does not depend on the will of the subjects (even system administrators). Compulsory access control is implemented in many versions of operating systems and DBMSs with enhanced security measures.
Cryptographic information protection - information protection by means of its cryptographic transformation.
Cryptographic techniques are currently basic to ensure reliable authentication of the parties to information exchange, protection.
TO means of cryptographic information protection(CIPF) includes hardware, software and hardware and software that implement cryptographic algorithms for transforming information in order to:
Protection of information during its processing, storage and transmission;
Ensuring the reliability and integrity of information (including using digital signature algorithms) during its processing, storage and transmission;
Generation of information used to identify and authenticate subjects, users and devices;
Generation of information used to protect the authenticating elements of the protected AS during their generation, storage, processing and transmission.
Cryptographic techniques include encryption and encoding of information... There are two main encryption methods: symmetric and asymmetric. In the first one, the same key (kept secret) is used for both encryption and decryption of data.
Very effective (fast and reliable) symmetric encryption methods have been developed. There is also a national standard for such methods - GOST 28147-89 “Information processing systems. Cryptographic protection. Algorithm for cryptographic transformation ".
Asymmetric methods use two keys. One of them, unclassified (it can be published together with other public information about the user), is used for encryption, the other (secret, known only to the recipient) - for decryption. The most popular of the asymmetric is the RSA method, based on operations with large (100-digit) primes and their products.
Cryptographic methods allow you to reliably control the integrity of both individual pieces of data and their sets (such as message flow); determine the authenticity of the data source; to guarantee the impossibility of refusing the committed actions ("non-repudiation").
Cryptographic integrity control is based on two concepts:
Electronic signature (ES).
A hash function is a hard-to-reverse data transformation (one-way function), usually implemented by means of symmetric block-binding encryption. The encryption result of the last block (depending on all previous ones) is the result of the hash function.
Cryptography as a means of protecting (closing) information is becoming increasingly important in commercial activities.
Various encryption tools are used to transform information: means of encrypting documents, including portable ones, means of encrypting speech (telephone and radio communications), means of encrypting telegraph messages and data transmission.
To protect commercial secrets in the international and domestic markets, various technical devices and sets of professional encryption and crypto-protection equipment for telephone and radio communications, business correspondence, etc. are offered.
Scramblers and maskers have become widespread, replacing the speech signal with digital data transmission. Means of protection for teletypes, telexes and faxes are produced. For these purposes, encryptors are used, made in the form of separate devices, in the form of attachments to devices or built into the design of telephones, fax modems and other communication devices (radio stations and others). To ensure the accuracy of transmitted electronic messages, electronic digital signatures are widely used.
1.1. This Policy for the use of cryptographic information protection tools ( Further - Politics ) determines the procedure for organizing and ensuring the functioning of encryption ( cryptographic) means designed to protect information that does not contain information constituting a state secret ( Further - CIPF, crypto-tool ) in the case of their use to ensure the security of confidential information and personal data during their processing in information systems.
1.2. This Policy has been developed in pursuance of:
- Federal law "About personal data" , regulations of the Government of the Russian Federation in the field of ensuring the security of personal data;
- Federal Law No. 63-FZ "About electronic signature" ;
- Order of the Federal Security Service of the Russian Federation No. 378 "On the approval of the Composition and content of organizational and technical measures to ensure the security of personal data during their processing in personal data information systems using cryptographic information protection tools necessary to fulfill the requirements established by the Government of the Russian Federation for the protection of personal data for each of the security levels";
- Order of FAPSI No. 152 " On approval of the Instruction on the organization and security of storage, processing and transmission through communication channels using cryptographic protection of information with limited access that does not contain information constituting a state secret»;
- Order of the FSB RF N 66 " On the approval of the Regulation on the development, production, sale and operation of encryption (cryptographic) information protection means (Regulation PKZ-2005) »;
1.3. This Policy applies to crypto tools designed to ensure the security of confidential information and personal data when processing them in information systems;
1.4. Cryptographic information security ( Further - SKZI ), which implement encryption and electronic signature functions, are used to protect electronic documents transmitted over publicly available communication channels, for example, the public Internet, or through dial-up communication channels.
1.5. To ensure security, it is necessary to use cryptographic information protection tools, which:
- allow integration into technological processes for processing electronic messages, provide interaction with application software at the level of processing requests for cryptographic transformations and issuing results;
- are supplied by developers with a complete set of operational documentation, including a description of the key system, rules for working with it, as well as justification of the necessary organizational and staff support;
- maintain the continuity of the processes of logging the operation of the cryptographic data protection system and ensuring the integrity of the software for the operating environment of the cryptographic data protection tool, which is a combination of hardware and software, together with which the cryptographic data protection tool operates normally and which can affect the fulfillment of the requirements for the cryptographic data protection tool;
- certified by an authorized government body or have permission from the FSB of Russia.
1.6. Cryptographic protection tools used to protect personal data must have a class not lower than KC2.
1.7. Cryptographic information protection tools are implemented on the basis of algorithms that meet the national standards of the Russian Federation, the terms of the contract with the counterparty.
1.8. CIPF, licenses, related key documents, instructions for CIPF are purchased by the organization independently or can be obtained from a third-party organization that initiates a secure document flow.
1.9. CIPF, including installation media, key documents, descriptions and instructions for CIPF, constitute a trade secret in accordance with the Regulation on Confidential Information.
The procedure for using cryptographic information protection tools
2.1. Installation and configuration of cryptographic information protection tools is carried out in accordance with operational documentation, instructions of the FSB of Russia, and other organizations participating in secure electronic document flow. At the end of the installation and configuration, the readiness of the cryptographic data protection system is checked for use with the drawing up of conclusions on the possibility of their operation and the input of the cryptographic data protection tool into operation.
Placement and installation of cryptographic information protection devices, as well as other equipment operating with crypto-devices, in secure rooms should minimize the possibility of uncontrolled access of unauthorized persons to these funds. Maintenance of such equipment and change of crypto keys are carried out in the absence of persons who are not allowed to work with the cryptographic data protection system. It is necessary to provide for organizational and technical measures to exclude the possibility of using the cryptographic data protection system by unauthorized persons. The physical location of the CIPF should ensure the security of the CIPF, preventing unauthorized access to the CIPF. Access of persons to the premises where the protective equipment is located is limited in accordance with the official necessity and is determined by the list approved by the director.
Embedding of KC1 and KC2 class crypto funds is carried out without control by the FSB of Russia ( if this control is not provided for by the terms of reference for the development (modernization) of the information system).
Embedding of KS3, KV1, KV2 and KA1 class crypto assets is carried out only under the control of the FSB of Russia.
Embedding of KC1, KC2 or KC3 class crypto assets can be carried out either by the user of the crypto tool with the appropriate license of the FSB of Russia, or by an organization holding the corresponding license of the FSB of Russia.
Embedding of a KV1, KV2 or KA1 class crypto facility is carried out by an organization licensed by the FSB of Russia.
Decommissioning of the cryptographic information protection system is carried out subject to procedures that ensure the guaranteed deletion of information, the unauthorized use of which may damage the business activities of the organization, and information used by information security tools, from permanent memory and from external media ( with the exception of archives of electronic documents and protocols of electronic interaction, the maintenance and preservation of which for a certain period is provided for by the relevant regulatory and (or) contractual documents) and is drawn up by the Act. SKZI destroy ( dispose of) by the decision of the owner of the crypto facility, and with the notification of the organization responsible in accordance with the organization of the one-by-one accounting of the crypto facility.
Slated for destruction ( recycling) CIPFs are subject to removal from the hardware with which they functioned. In this case, crypto assets are considered withdrawn from the hardware if the procedure for removing the software of the crypto assets provided for in the operational and technical documentation for the cryptographic information protection tool is executed and they are completely disconnected from the hardware.
Suitable for further use nodes and parts of general-purpose hardware, not specifically designed for the hardware implementation of cryptographic algorithms or other cryptographic information protection functions, as well as equipment that works with cryptographic means ( monitors, printers, scanners, keyboards, etc.), it is allowed to use after the destruction of the CIPF without restrictions. In this case, the information that can remain in the equipment memory devices ( e.g. in printers, scanners), must be securely removed ( erased).
2.2. The operation of the CIPF is carried out by persons appointed by the order of the director of the organization and trained to work with them. In the presence of two or more CIPF users, responsibilities between them are distributed taking into account personal responsibility for the safety of crypto assets, key, operational and technical documentation, as well as for the assigned work areas.
Crypto users are obliged to:
- not to disclose information to which they are admitted, including information about cryptographic information protection devices and other protection measures;
- not to disclose information about key documents;
- do not allow making copies of key documents;
- prevent the output of key documents on the display ( monitor) a personal computer or printer;
- do not allow extraneous information to be recorded on the key carrier;
- prevent the installation of key documents in other personal computers;
- comply with the requirements for ensuring the security of information, the requirements for ensuring the security of cryptographic information protection tools and key documents to them;
- to report on the attempts of unauthorized persons that have become known to them to obtain information about the cryptographic information protection system used or key documents to them;
- immediately notify about the facts of loss or shortage of cryptographic information protection tools, key documents to them, keys from premises, storage facilities, personal seals and other facts that may lead to the disclosure of protected information;
- hand over cryptographic information protection tools, operational and technical documentation to them, key documents upon dismissal or suspension from duties related to the use of cryptographic means.
The security of information processing using cryptographic information protection tools is ensured by:
- observance of confidentiality by users when handling information that is entrusted to them or became known from work, including information about the functioning and procedure for ensuring the security of the applied cryptographic information protection system and key documents to them;
- accurate fulfillment of the requirements for information security by the CIPF users;
- reliable storage of operational and technical documentation for CIPF, key documents, information carriers of limited distribution;
- timely detection of attempts by unauthorized persons to obtain information about the protected information, about the cryptographic information protection devices used or key documents to them;
- immediate adoption of measures to prevent the disclosure of protected information, as well as its possible leakage in case of revealing the facts of loss or shortage of cryptographic data protection devices, key documents to them, certificates, passes, keys to premises, storages, safes ( metal cabinets), personal seals, etc.
If it is necessary to transfer service messages of limited access by technical means of communication concerning the organization and operation of the cryptographic information protection system, these messages must be transmitted only with the use of cryptographic means. Transfer of crypto keys by technical means of communication is not allowed, with the exception of specially organized systems with decentralized supply of crypto keys.
CIPFs are subject to accounting using indices or conventional names and registration numbers. The list of indices, conventional names and registration numbers of crypto assets is determined by the Federal Security Service of the Russian Federation.
Used or stored CIPF, operational and technical documentation to them, key documents are subject to one-by-one accounting. The form of the Register of CIPF is given in Appendix No. 1, the Register of key carriers in Appendix No. 2 to this Policy. At the same time, software cryptographic information protection tools should be taken into account together with the hardware with which their regular operation is carried out. If hardware or hardware-software cryptographic means are connected to the system bus or to one of the internal interfaces of the hardware, then such cryptographic means are also taken into account together with the corresponding hardware.
The unit of one-by-one accounting of key documents is considered to be a key reusable medium, a key notebook. If one and the same key carrier is repeatedly used to record crypto keys, then it should be registered separately each time.
All received copies of crypto-tools, operational and technical documentation for them, key documents must be issued against receipt in the appropriate register of the crypto-tools users who are personally responsible for their safety.
The transfer of cryptographic information protection tools, operational and technical documentation to them, key documents is allowed only between users of cryptographic means and (or) the responsible user of cryptographic means against receipt in the corresponding logs of one-to-one accounting. Such transfer between users of cryptographic facilities must be authorized.
Storage of CIPF installation media, operational and technical documentation, key documents is carried out in cabinets ( boxes, storages) for individual use in conditions precluding uncontrolled access to them, as well as their unintentional destruction.
The hardware with which the regular operation of the cryptographic information protection tool is carried out, as well as the hardware and hardware-software cryptographic information protection tool, must be equipped with means of control over their opening ( sealed, sealed). Place of sealing ( sealing) cryptographic means, hardware must be such that it can be visually controlled. If there is a technical feasibility for the duration of the absence of users of the crypto-means, these means must be disconnected from the communication line and put into sealed storages.
Changes to the cryptographic information protection software and technical documentation on the cryptographic information protection system are carried out on the basis of the updates received from the manufacturer of the cryptographic information protection system and documented updates with the fixation of checksums.
Operation of the cryptographic information protection system involves maintaining at least two backup copies of software and one backup copy of key media. The restoration of the CIPF serviceability in emergency situations is carried out in accordance with the operational documentation.
2.3. The production of key documents from the initial key information is carried out by responsible users of cryptographic information protection tools, using standard crypto tools, if such a possibility is provided for by the operational and technical documentation with a license from the FSB of Russia for the production of key documents for crypto tools.
Key documents can be delivered by courier ( including departmental) communication or with specially designated responsible users of crypto assets and employees, subject to measures that exclude uncontrolled access to key documents during delivery.
To send key documents, they must be placed in strong packaging, excluding the possibility of physical damage and external impact. The packages indicate the responsible user for whom these packages are intended. These packages are marked "Personally". Packages are sealed in such a way that it is impossible to extract the contents from them without disturbing the packages and seal imprints.
Prior to initial expulsion ( or return) the addressee is informed by a separate letter a description of the packages and seals sent to him, with which they can be sealed.
To send key documents, a cover letter is prepared, which must indicate what is being sent and in what quantity, account numbers of documents, as well as, if necessary, the purpose and procedure for using the sent item. The cover letter is enclosed in one of the packages.
The received packages are opened only by the responsible user of the crypto assets for which they are intended. If the contents of the package received do not correspond to the one specified in the covering letter or the package itself and the seal - their description ( imprint), as well as if the package is damaged, as a result of which there is free access to its contents, then the recipient draws up an act that is sent to the sender. Key documents received with such items shall not be used until instructions are received from the sender.
If defective key documents or crypto keys are found, one copy of the defective product should be returned to the manufacturer in order to establish the causes of the incident and their elimination in the future, and the remaining copies should be stored until additional instructions from the manufacturer are received.
The receipt of key documents must be confirmed to the sender in accordance with the procedure specified in the covering letter. The sender is obliged to control the delivery of his items to the addressees. If the appropriate confirmation has not been received from the addressee in a timely manner, the sender must send him a request and take measures to clarify the location of the items.
The order for the production of the next key documents, their production and distribution to the places of use for the timely replacement of the existing key documents is made in advance. The instruction on the commissioning of the next key documents is given by the responsible user of the crypto assets only after receiving confirmation from them about the receipt of the next key documents.
Key documents that have not been used or taken out of action are to be returned to the responsible user of the crypto assets or, at his instruction, must be destroyed on the spot.
Destruction of crypto keys ( original key information) can be done by physically destroying the key carrier on which they are located, or by erasing ( destruction) crypto keys ( original key information) without damaging the key carrier ( to make it reusable).
Cryptokeys ( original key information) are erased according to the technology adopted for the corresponding reusable key carriers ( floppy disks, CD-ROMs, Data Key, Smart Card, Touch Memory, etc.). Direct actions to erase crypto keys ( original key information( original key information).
Key carriers are destroyed by inflicting irreparable physical damage to them, excluding the possibility of their use, as well as by restoring key information. Direct actions to destroy a specific type of key carrier are regulated by operational and technical documentation for the corresponding cryptographic information protection system, as well as by the instructions of the organization that recorded the crypto keys ( original key information).
Paper and other combustible key media are destroyed by incineration or using any paper cutting machines.
Key documents are destroyed within the timeframes specified in the operational and technical documentation for the relevant CIP. The fact of destruction is documented in the appropriate individual registration journals.
Destruction according to the act is carried out by a commission of at least two people. The act specifies what is destroyed and in what quantity. At the end of the act, a final record is made (in numbers and in words) about the number of names and copies of destroyed key documents, installing CIPF media, operational and technical documentation. Corrections in the text of the act must be agreed and certified by the signatures of all members of the commission who took part in the destruction. The destruction carried out shall be noted in the corresponding individual registration logs.
Cryptokeys in respect of which there is a suspicion of compromise, as well as other cryptokeys acting in conjunction with them, must be immediately withdrawn from action, unless a different procedure is stipulated in the operational and technical documentation of the CIPF. In emergency cases, when there are no crypto keys to replace the compromised ones, it is allowed, by the decision of the responsible user of the crypto tools, agreed with the operator, to use the compromised crypto keys. In this case, the period of use of compromised crypto keys should be as short as possible, and the protected information should be as less valuable as possible.
Violations that may lead to the compromise of crypto keys, their components or transmitted ( stored) with their use of data, users of crypto-funds are obliged to inform the responsible user of the crypto-funds.
Inspection of reusable key carriers by unauthorized persons should not be considered as a suspicion of compromising crypto keys, if at the same time the possibility of copying them was excluded ( reading, reproduction).
In cases of shortage, non-presentation of key documents, as well as uncertainty of their location, the responsible user takes urgent measures to search for them and localize the consequences of the compromise of key documents.
Key system management procedure
Registration of persons with the rights to manage keys is carried out in accordance with the operational documentation for the CIPF.
Key management is an information process that includes three elements:
- key generation;
- accumulation of keys;
- distribution of keys.
The organization's information systems use special hardware and software methods for generating random keys. As a rule, sensors of pseudo random numbers are used ( Further - PSCH ), with a sufficiently high degree of randomness of their generation. Software key generators are quite acceptable, which calculate the PRNG as a complex function of the current time and ( or) of the number entered by the user.
The accumulation of keys means the organization of their storage, accounting and disposal.
Private keys should not be written explicitly on media that can be read or copied.
All information about the keys used must be stored encrypted. Keys that encrypt key information are called master keys. Each user must know the master keys by heart, it is forbidden to store them on any material media.
For the condition of information security, it is necessary to periodically update key information in information systems. In this case, both regular keys and master keys are reassigned.
When distributing keys, the following requirements must be met:
- efficiency and accuracy of distribution;
- hidden keys to be distributed.
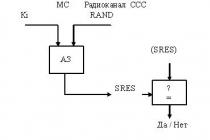
An alternative is for two users to obtain a shared key from a central authority, the Key Distribution Center (KDC), with which they can communicate securely. To organize the exchange of data between the CCC and the user, the latter is assigned a special key during registration, which encrypts messages transmitted between them. Each user is assigned a separate key.
KEY MANAGEMENT BASED ON PUBLIC KEY SYSTEMS
Before using a public key cryptosystem to exchange common private keys, users must exchange their public keys.
Public key management can be organized through an online or offline directory service, and users can also exchange keys directly.
Monitoring and control of the use of cryptographic information protection tools
To increase the level of security during the operation of the cryptographic information system, the system should implement monitoring procedures that record all significant events that took place in the process of exchanging electronic messages and all information security incidents. The description and list of these procedures should be established in the operational documentation for the CIPF.
Control over the use of cryptographic information protection devices provides:
- control over the compliance of setting and configuring information security tools, as well as hardware and software that can affect the fulfillment of requirements for information security tools, regulatory and technical documentation;
- monitoring compliance with the rules for storing restricted information used in the operation of information security tools ( in particular, key, password and authentication information);
- control of the ability of unauthorized persons to access information security means, as well as to hardware and software that can affect the fulfillment of requirements for information security means;
- monitoring compliance with the rules for responding to information information incidents ( about the facts of loss, compromise of key, password and authentication information, as well as any other information of limited access);
- control of compliance of hardware and software CIPF and documentation for these tools with reference samples ( supplier warranties or controls to self-establish such compliance);
- control of the integrity of hardware and software tools for cryptographic information protection systems and documentation for these tools during storage and commissioning of these tools ( using both the control mechanisms described in the CIPF documentation and using organizational).
![]()
Download ZIP file (43052)
The documents came in handy - put "like" or:
Corporate encryption tools introduced by AST can support GOST encryption algorithms and provide the necessary classes of crypto protection, depending on the required degree of protection, regulatory framework and requirements for compatibility with other, including external systems.
Means of cryptographic information protection (CIP) are an important component in ensuring information security and allow you to guarantee a high level of data safety, even in the event of encrypted electronic documents falling into the hands of third parties, as well as in case of theft or loss of information carriers with them. Cryptographic information protection tools are used today in almost every company - more often at the level of interaction with automated banking systems and state information systems; less often - for storing and exchanging corporate data. Meanwhile, it is the latest use of encryption tools that protects businesses from dangerous leaks of critical information with a guarantee of up to 99%, even taking into account the human factor.
Functionally, the need for the use of cryptographic information protection tools is also determined by the ever-growing popularity of electronic document management, archiving and paperless interaction tools. The importance of documents processed in such systems dictates the obligation to ensure high security of information, which cannot be done without the use of encryption and electronic signatures.
The introduction of cryptographic information protection tools into corporate practice provides for the creation of a software and hardware complex, the architecture and composition of which is determined based on the needs of a particular customer, legal requirements, tasks and necessary methods, and encryption algorithms. This may include software components of encryption (cryptographic providers), VPN organization tools, authentication tools, tools for generating and verifying keys and EDS used to organize legally significant document flow, hardware storage media.
Corporate encryption tools introduced by AST can support GOST encryption algorithms and provide the necessary classes of crypto protection, depending on the required degree of protection, regulatory framework and requirements for compatibility with other, including external systems. At the same time, encryption tools provide protection for the entire set of information components - files, directories with files and archives, physical and virtual media, servers and storage systems as a whole.
The solution will be able to provide a full range of measures for the reliable protection of information during its storage, transmission, use, as well as for the management of the cryptographic information protection system, including:
- Ensuring confidentiality of information
- Ensuring the integrity of information
- Guaranteed authenticity of information
- Targeted information protection, including:
- Encryption and decryption
- Creation and verification of EDS - Flexibility of configuration, management and use of cryptographic information protection tools
- Protection of cryptographic information protection devices, including monitoring and detecting cases of malfunction, attempts of unauthorized access, cases of compromised keys.
Completed projects
Related services:
-
Event monitoring and information security incident management
The most important factor in ensuring information security (IS) is the availability of complete and reliable information about events,
[...] -
Providing network security and perimeter protection
The network infrastructure technologically underlies all corporate IT systems and is a transport artery for information,
[...] -
Protection against targeted attacks
One of the most serious and dangerous threats to business from the point of view of information security (IS) is targeted
[...] -
APCS protection
An automated process control system (APCS) in production is a fundamental solution,
[...] -
Vulnerability analysis and management systems
As there are no absolutely healthy people, there are no absolutely secure information systems. IT infrastructure components
[...] -
Information Leakage Protection (DLP System)
Any organization has restricted access documents containing certain confidential information. Their falling into strangers